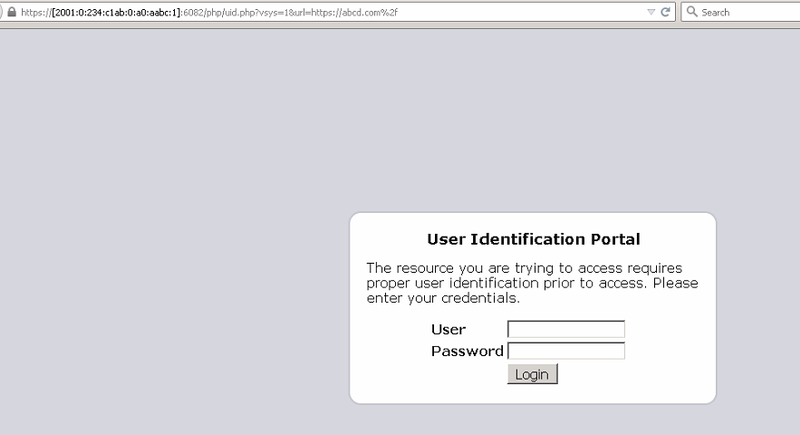
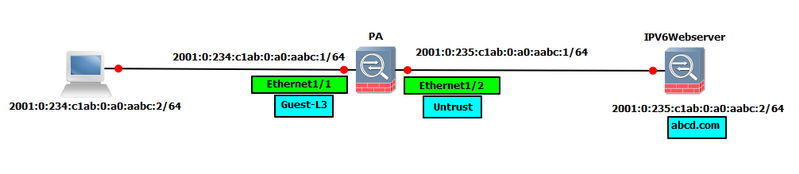
We can configure captive portal for websites that are using the IPV6 address. The configuration is similar to that of IPV4 address. Here in the topology: We have a web server abcd.com which has an IPV6 address. Both the Palo Alto Networks firewall (PA) and the test system have IPV6 addresses configured.
Topology:
Please use the following steps to configure captive portal for an environment that has IPV6 addresses.
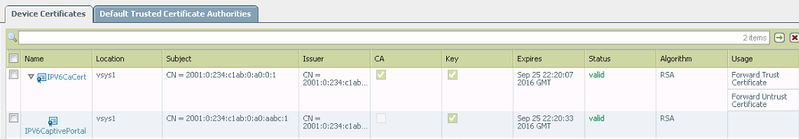
Step 1. Create a certificate. This certificate will be used by the firewall to give to the end user when they are trying to access websites.
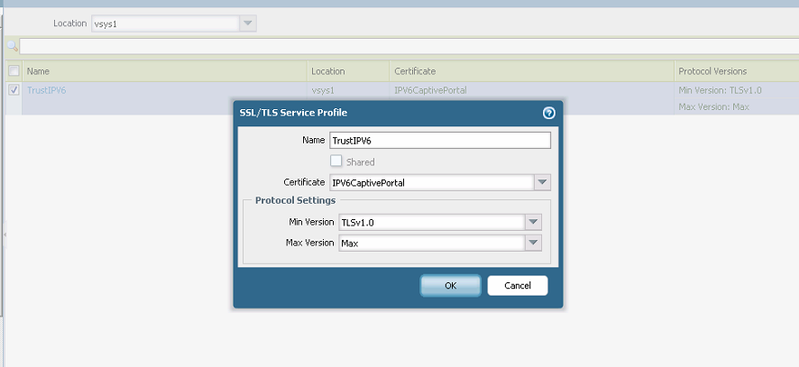
Step 2. Create the server profile, name it ‘TrustIPV6,’ and call/refer to the certificate you created in Step 1, which was 'IPV6CaptivePortal.' See below.
Step 3. Authentication profile: This authentication profile will be user used to authenticate the users.
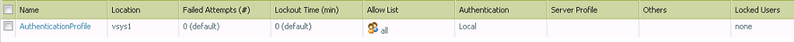
Step 4. Captive portal setting: Configure captive portal under Device > User Identification > Captive Portal. Specify the SSL/TLS service profile, authetication profile that we have created earlier. Specify the redirect host to which the web traffic will be redirected when the user tries to access the websites.
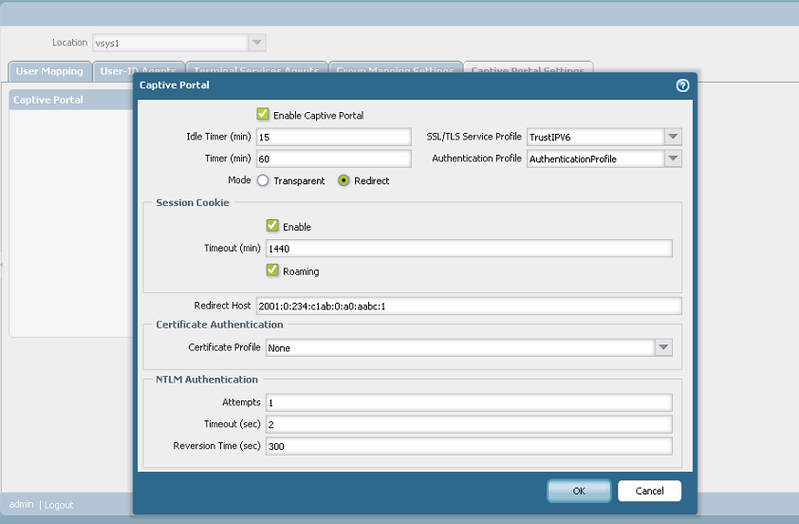
Step 5. Zone: Enable the user identification on the zone.
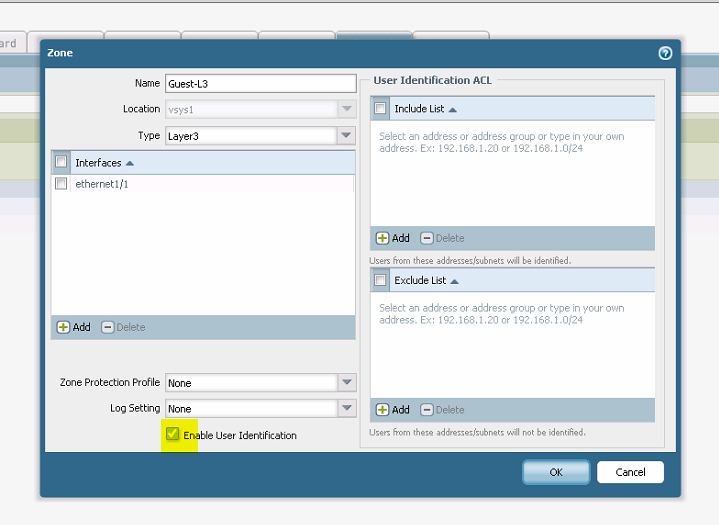
Step 6. Management profile: Create a management profile with response page enabled.
Step 7. Interface: Call the management profile into the interface configuration.

Step 8. Captive Portal rule: Create a captive portal rule for interesting traffic.

- Enable decryption for https website.
- Allow interesting traffic by security policies.
Output: