Please refer to this document on How to Configure DNS Proxy on a Palo Alto Networks Firewall.
In this example, the DNS proxy is enabled on Ethernet 1/1 with IP address 10.50.240.72, which is the DNS server for the internal host machines.
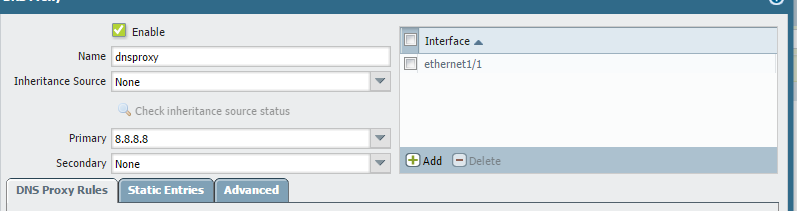

Since the DNS traffic from the host will take an intrazone policy, we need to enable Log at Session End in the default intrazone policy. Subsequently, you can create a new policy.
DNS servers on the host machines -- 10.50.240.72.
C:\Users\Administrator>nslookup
DNS request timed out.
timeout was 2 seconds.
Default Server: UnKnown
Address: 10.50.240.72 this is my dns server
- Test Machine's IP address is 10.50.240.137
- The firewall's trust interface E1/1 is 10.50.240.72, which is the interface on which the DNS proxy is enabled, and the DNS server for the internal servers.
Method 1:
Whenever hosts do an nslookup or users go to any domain, you will notice sessions, which verify DNS proxy is working fine.
Taranf@chnlab-fw74> show session all filter application dns-base
-----------------------------------------------------------------------------------------
ID Application State Type Flag Src[Sport]/Zone/Proto (translated IP[Port])
Vsys Dst[Dport]/Zone (translated IP[Port])
-----------------------------------------------------------------------------------------
95124 dns ACTIVE FLOW 10.50.240.137[47615]/Untrust-L3/17 (10.50.240.137[47615])
vsys1 10.50.240.72[53]/Untrust-L3 (10.50.240.72[53])
These sessions are from the internal host machine whose IP address is 10.50.240.137, to the firewall's IP address, 10.50.240.72 (E1/1).
The above session shows the firewall acting as a man-in-middle for the DNS queries. However, on the firewall, we have configured the DNS server as 8.8.8.8, so now the firewall is contacting the DNS server on behalf of the internal hosts.
Method 2:
- Enter the following command:
>show dns-proxy cache all
(If there are entries, that means the DNS proxy is working.)
- If you want to clear the cache and make sure no old cache is there, enter the following command:
>clear dns-proxy cache all
- Do some nslookups or open google.com and check the DNS cache using the command:
>show dns-proxy cache all
(If there are cached entries, then DNS proxy is working fine.)