There may be cases where analysis/verification is required to determine whether traffic is being sent/received via the management interface. One such example would be during authentication testing to verify whether requests are being sent from the device to the LDAP or Radius server. Another example would be to determine whether a device is being polled/reachable through a SNMP server. Starting with PAN-OS 5.0 it is possible to know PCAP traffic to/from the management interface. The option is strictly CLI based utilizing tcpdump.
Example below:
As captures are strictly/implicitly utilizing the management interface, there is no need to manually specify interfaces as with a traditional tcpdump. For example:
admin@myNGFW> tcpdump filter "host 10.16.0.106 and not port 22"
Press Ctrl-C to stop capturing
tcpdump: listening on eth0, link-type EN10MB (Ethernet), capture size 96 bytes
Note: Filters must be enclosed in quotes, as in:
> tcpdump filter "host 10.16.0.106 and not port 22"
When a capture is complete, press Ctrl-C to stop capturing:
admin@myNGFW> tcpdump filter "host 10.16.0.106 and not port 22"
Press Ctrl-C to stop capturing
tcpdump: listening on eth0, link-type EN10MB (Ethernet), capture size 96 bytes
^C 6 packets captured
12 packets received by filter
0 packets dropped by kernel
To view the PCAP on the CLI run the view-pcap command. For example:
admin@myNGFW> view-pcap mgmt-pcap mgmt.pcap
15:42:57.834414 IP 10.16.0.106.https > 10.192.1.0.61513: P 196197148:196197179(31) ack 2821691363 win 66 <nop,nop,timestamp 9463094 700166797>
15:42:57.834477 IP 10.16.0.106.https > 10.192.1.0.61513: F 31:31(0) ack 1 win 66 <nop,nop,timestamp 9463094 700166797>
15:42:57.834910 IP 10.192.1.0.61513 > 10.16.0.106.https: . ack 31 win 4095 <nop,nop,timestamp 700231236 9463094>
15:42:57.834933 IP 10.192.1.0.61513 > 10.16.0.106.https: . ack 32 win 4095 <nop,nop,timestamp 700231236 9463094>
15:42:58.142807 IP 10.192.1.0.61513 > 10.16.0.106.https: F 1:1(0) ack 32 win 4096 <nop,nop,timestamp 700231542 9463094>
15:42:58.142831 IP 10.16.0.106.https > 10.192.1.0.61513: . ack 2 win 66 <nop,nop,timestamp 9463125 700231542>
Following are a few filter examples (though NOT limited solely to these options) which can be referenced/utilized/applied:
- Filter By Port
> tcpdump filter "port 80" - Filter By Source IP
> tcpdump filter "src x.x.x.x" - Filter By Destination IP
> tcpdump filter "dst x.x.x.x" - Filter By Host (src & dst) IP
> tcpdump filter "host x.x.x.x" - Filter By Host (src & dst) IP, excluding SSH traffic
> tcpdump filter "host x.x.x.x and not port 22"
Additionally, you can manually export the PCAP file. If PAN-OS is 10.2 or later, it can be exported from the web interface.
- From the web interface : Device > Support > Debug and Management Pcap Files > Download Debug and Management Pcap Files
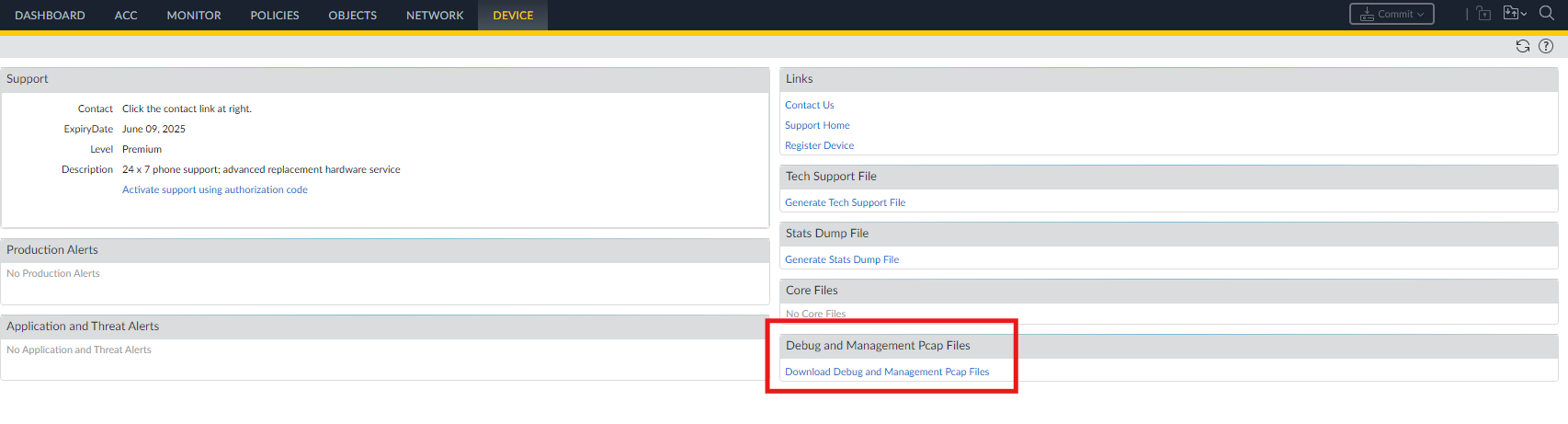
- Then click "mgmt.pcap"
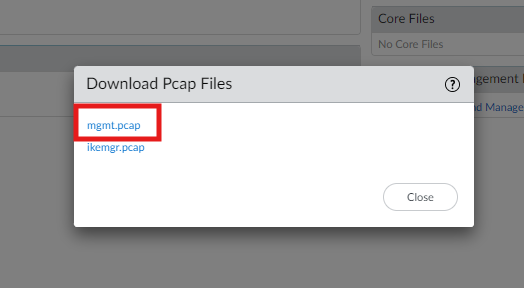
If PAN-OS is 10.1 or older, it can be exported via SCP or TFTP, i.e.:
> scp export mgmt-pcap from mgmt.pcap to
<value> Destination (username@host:path)
> tftp export mgmt-pcap from mgmt.pcap to
<value> tftp host
Note: By default, there is a maximum limit of 68 bytes (Snap Length) per packet on PA-200, PA-500 and PA-2000. For the PA-3000, PA-4000 and PA-5000, the default limit is 96 bytes per packet. To extend this limit, use the "snaplen" option. If you want to capture the complete packet, use the option snaplen 0 with the tcpdump
admin@myNGFW> tcpdump snaplen
<value> <0-65535> Snarf snaplen bytes of data from each packet. (0 means use the required length to catch whole packets)
admin@myNGFW> tcpdump snaplen 0
Press Ctrl-C to stop capturing
tcpdump: listening on eth0, link-type EN10MB (Ethernet), capture size 65535 bytes
See Also
Tcpdump Packet Capture Truncated
owner: bryan