Overview
When deploying Zone Protection profiles to detect penetration scans, the corresponding traffic must be allowed by Security Policies. Otherwise, the Zone Protection profiles will not generate threat logs and the offending traffic will be dropped because of security rule that denies the traffic.
Details
An example Zone Protection Profile is shown below. The name of this profile is "Test-Zone-Prot".
- Flood Protection tab:
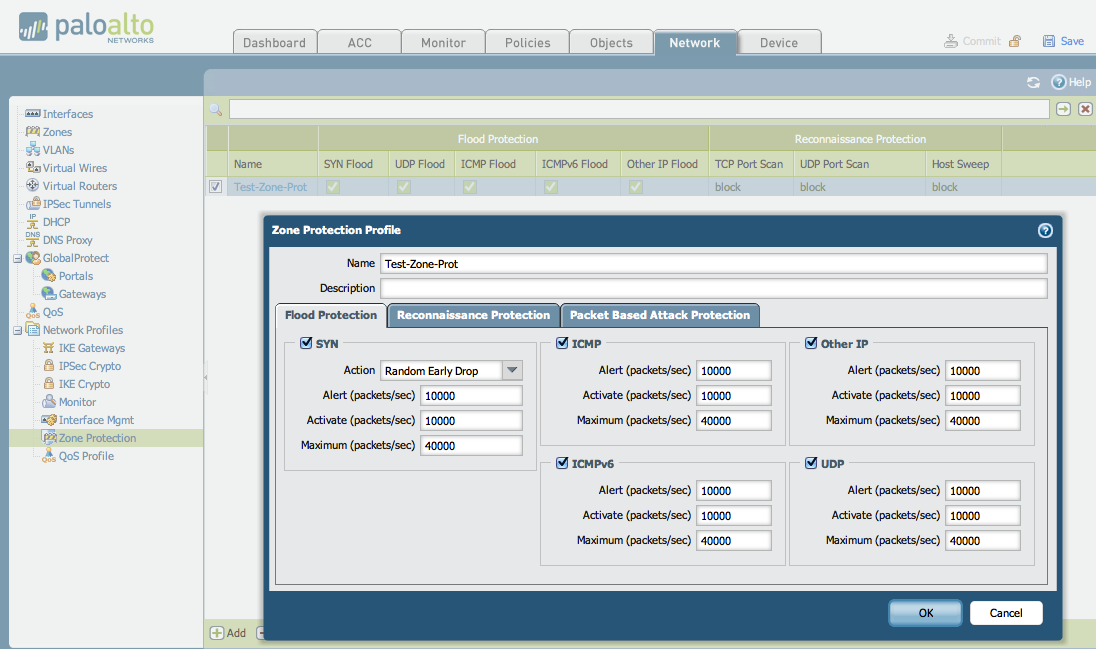
- Reconnaissance Protection tab:
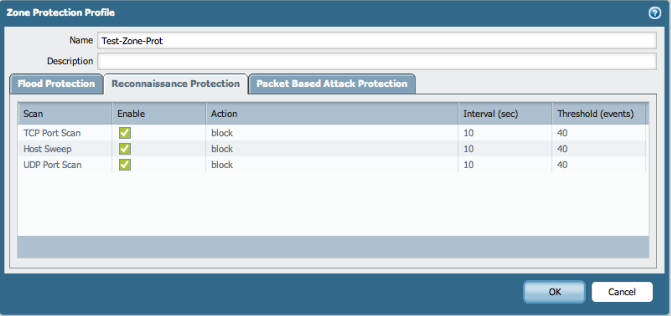
- Packet Based Attack Protection tab:
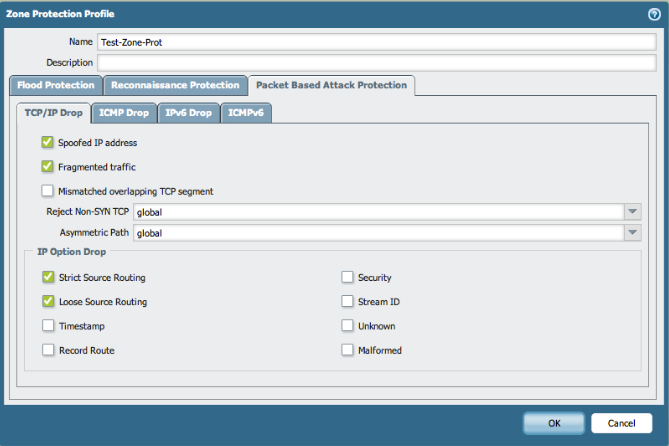
The above Zone Protection profile, "Test-Zone-Prot", is applied to the zone for are penetration scanning. The goal is to enable scanning on ethernet1/3:

Security Policy Set to Allow Traffic
For demonstration purposes, the active Security Policy is set to allow all traffic. This would typically not be the case for production environments.

With the above configuration, the first NMAP penetration scan results are as follows:
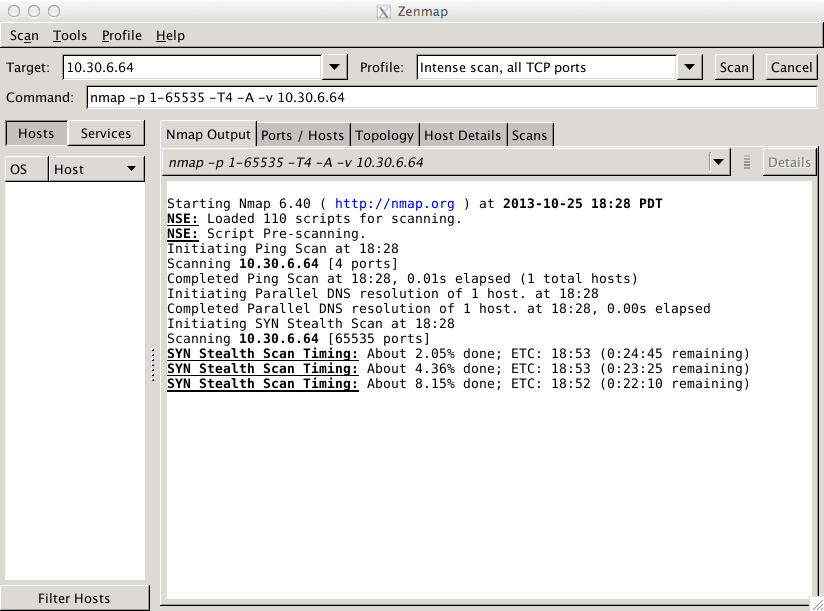
The resulting Threat logs (Monitor > Logs > Threat) are shown below:
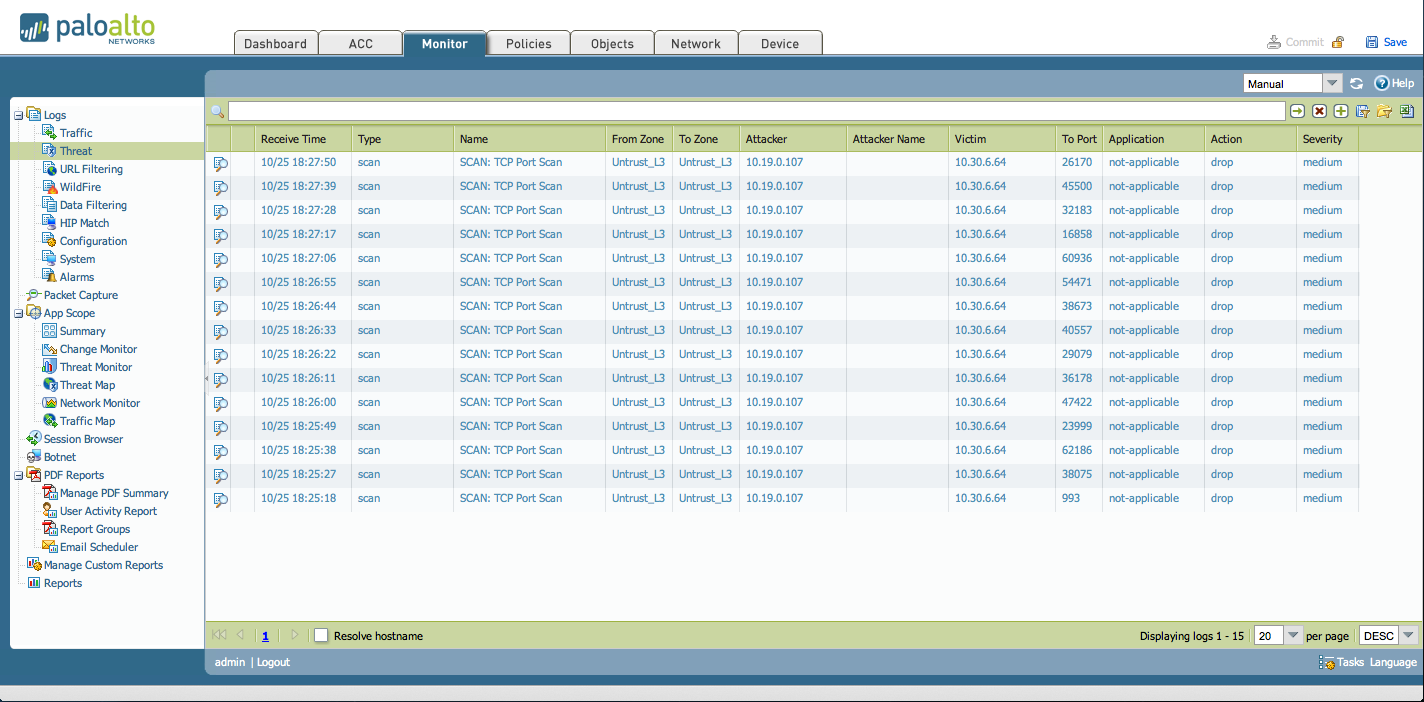
As seen above, the Zone Protection Profile is enabled and functions as expected.
Security Policy Set to Deny Traffic
If there is no security policy to allow traffic to the target interface then this prevents the zone protection to create threat logs during penetration scan on that interface.
In this configuration, the last Security Policy is configured to deny traffic.

The results for an NMAP penetration scan for this configuration is shown below:
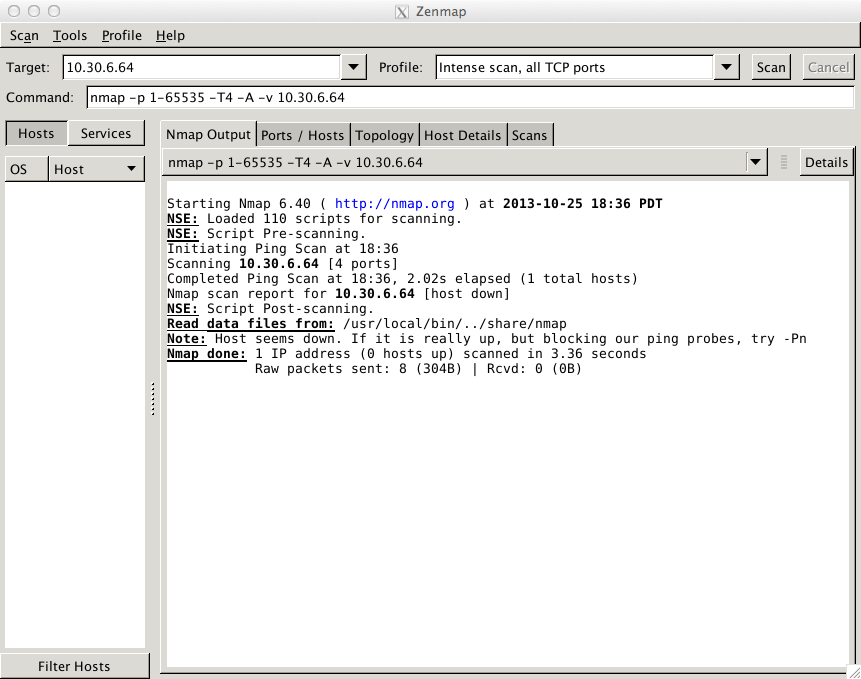
The resulting Threat Logs are empty:
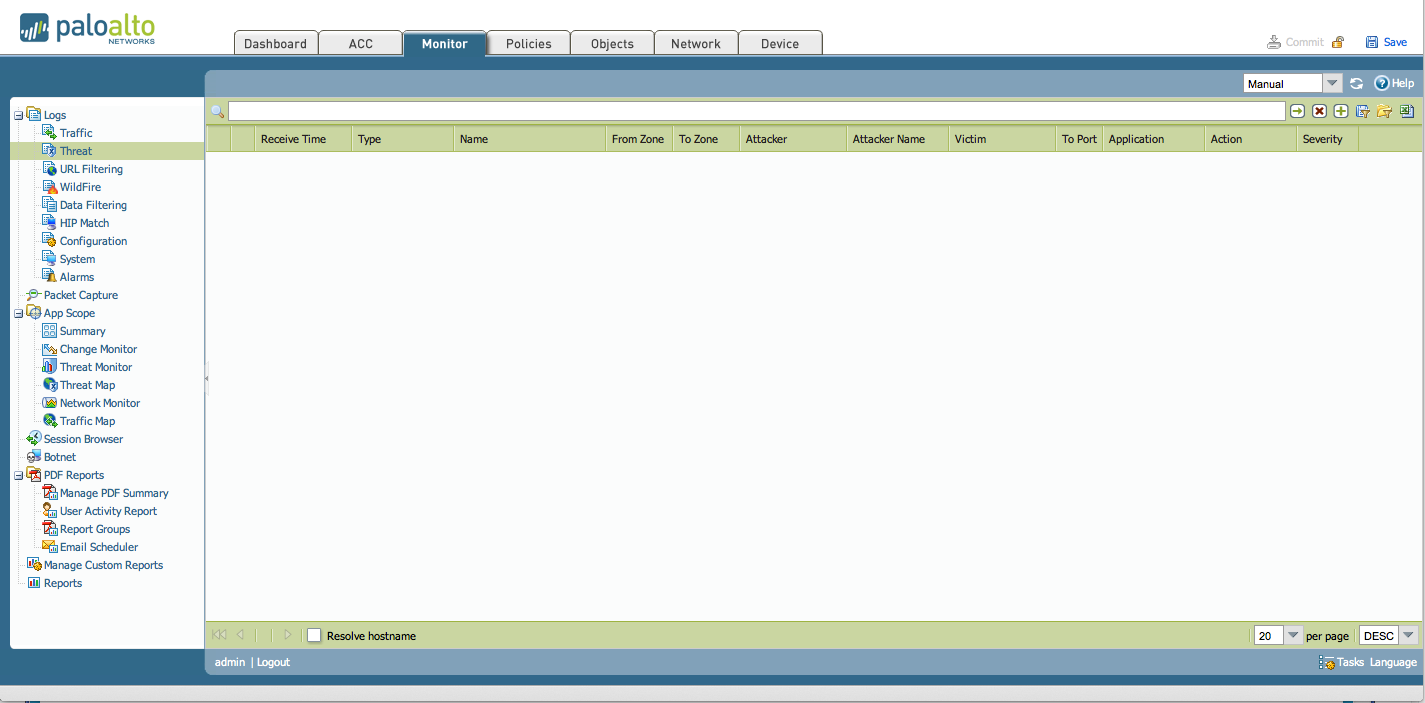
There are no threat logs as the traffic was dropped immediately by the "deny" security policy.
Note: There will only be entries in the Threat logs due to a Zone Protection profile, if the scans are run against "open ports" on the external zone.
owner: cchristiansen