Overview
Currently, Palo Alto Networks firewall does not look inside IP-in-IP packets. The firewall only routes it according to the outer header of packets.
Shown below is an example of show session id for IP-in-IP:
> show session id 1
Session 1
c2s flow:
source: 10.215.15.247 [untrust]
dst: 10.215.15.174
proto: 4
sport: 20033 dport: 20033
state: ACTIVE type: FLOW
src user: unknown
dst user: unknown
s2c flow:
source: 10.215.15.174 [trust]
dst: 10.215.15.247
proto: 4
sport: 20033 dport: 20033
state: ACTIVE type: FLOW
src user: unknown
dst user: unknown
start time : Wed Jan 7 19:07:45 2015
timeout : 30 sec
time to live : 27 sec
total byte count(c2s) : 33844960
total byte count(s2c) : 0
layer7 packet count(c2s) : 412712
layer7 packet count(s2c) : 0
vsys : vsys1
application : ip-in-ip
rule : rule1
session to be logged at end : True
session in session ager : True
session synced from HA peer : False
layer7 processing : completed
URL filtering enabled : False
session via syn-cookies : False
session terminated on host : False
session traverses tunnel : False
captive portal session : False
ingress interface : ethernet1/1
egress interface : ethernet1/2
session QoS rule : N/A (class 4)
session tracker stage l7proc : ctd app has no decoder
paloalto@PA-5050>
Note: IP-in-IP Encapsulation: This protocol provides a mechanism to encapsulate an IP header with an outer IP header for tunnelling.
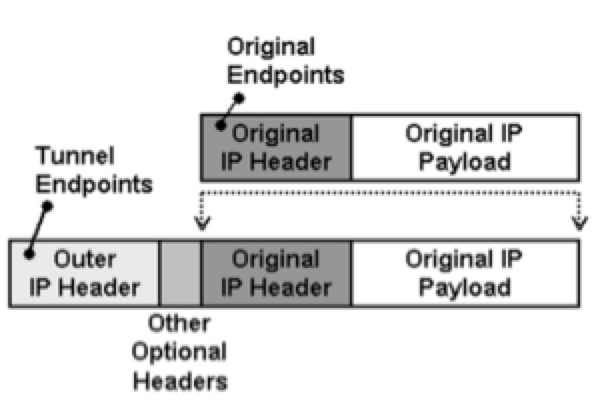
See Also
IP Encapsulation Within IP
owner: dkim