
Palo Alto Networks support engineers receive questions on a regular basis about NAT and something called U-Turn NAT.
NAT is Network Address Translation, and it is used to help translate a Private IP (RFC 1918) into a Public IP for privacy, because it
hides behind another IP, and the fact that a Private IP address is not routable on the Internet. This is known as Source NAT or Hide NAT.
We also have Destination NAT, which allows the firewall to advertise it's Untrust IP (or another IP) to then be translated to an Internal host
or web server.
U-Turn NAT refers to the logical path that traffic appears to travel when accessing an internal resource when they resolve thier external address. U-turn NAT is often used in a network where internal users need to access an internal DMZ server using the server’s external public IP address.
Satish recently posted about a NAT issue that he was experiencing in a recent discussion.
NAT Issue
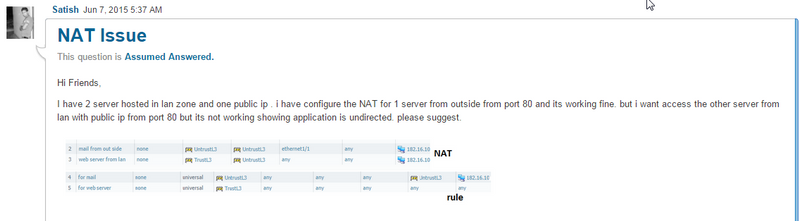
Satish was experiencing an issue with NAT that might be resolved with the use of U-Turn NAT.
More info
Lets look at the following layout when we are talking about NAT and U-Turn NAT.
3 zones:
Trust Zone - e1/4 192.168.1.4/24
DMS Zone - e1/13 10.1.1.1/24
Untrust Zone - e1/3 203.0.113.100/24
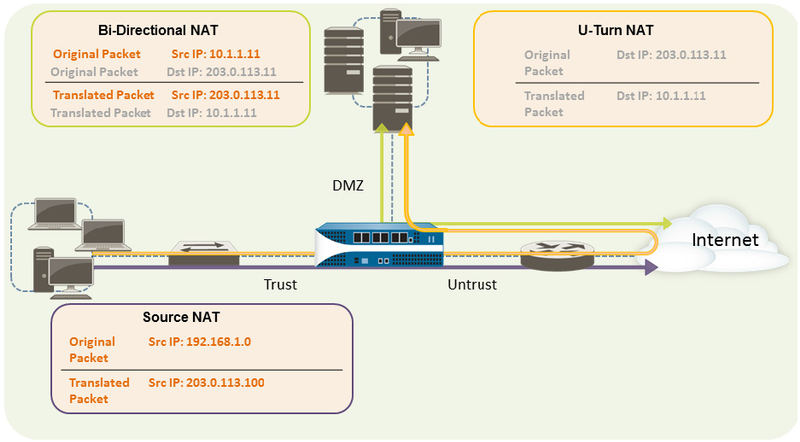
Source NAT
To enable the clients on the internal network to access resources on the Internet, the internal 192.168.1.0
addresses will need to be translated to publicly routable addresses. In this case, we will configure source
NAT, using the egress interface address, 203.0.113.100, as the source address in all packets that leave the
firewall from the internal zone.
Destination NAT
To enable the web server—which has both a private IP address on the DMZ network and a public-facing
address for access by external users—to both send and receive requests, the firewall must translate the
incoming packets from the public IP address to the private IP address and the outgoing packets from the
private IP address to the public IP address. On the firewall, you can accomplish this with a single
bi-directional static source NAT policy.
U-Turn NAT
To enable clients on the internal network to access the public web server in the DMZ zone, we will need to
configure a NAT rule that redirects the packet from the external network, where the original routing table
lookup will determine it should go based on the destination address of 203.0.113.11 within the packet, to
the actual address of the web server on the DMZ network of 10.1.1.11. To do this you must create a NAT
rule from the trust zone (where the source address in the packet is) to the untrust zone (where the original
destination address is) to translate the destination address to an address in the DMZ zone.
You also need to have a rule that also allows traffic from the Trust to the DMZ to access the web server in
question.
For more information, please see this document:
How to Configure U-Turn NAT
We always welcome comments and questions below in the comments section.
Thanks for reading,
Joe Delio