Creating Custom App-IDs Case Study: Fortnite
Resolution
Issue
Fortnite is an online multiplayer game, for PC and other devices. This game is common amongst school age students and is one of many such games that boarding schools need to accommodate on their network.
Pre-defined App-IDs are provided for a number of well known games. However, for very new or uncommon games, App-IDs may not be available. In addition, these games are frequently updated, and communication formats can change rapidly. Therefore, even the games with pre-defined App-IDs may fail until the change can be identified and new signatures are released. Palo Alto Networks provides the ability to create custom App-IDs, allowing administrators to use a wide range of factors within the network traffic to identify applications.
Much of the network traffic associated with such games run across common network protocols, such as HTTPS. However, some traffic, particularly the in-game communication requires faster protocols with less overhead. Therefore, it is common to observe UDP streams over high ports, classified by the NGFW as ‘Unknown-UDP’.
Schools and other organisations commonly have a requirement to block such unidentified traffic, and therefore it is necessary to identify and create custom App-IDs for these traffic patterns. Due to the requirement for this traffic to be as lightweight as possible, the amount of arbitrary content in these messages that can be used as a signature is low.
Process
Find the unidentified traffic
Most online games communicate in a variety of different ways. For example, when the game is first launched, HTTPS traffic is used to authenticate the user to an accounting server, and provide the game client with information about currently running games and servers, commonly known as a lobby. When the game itself starts, a communication session is established to the game server to deliver information about player movements and game state. Most of this traffic is sent to un-predictable locations, and some traffic is sent across unpredictable ports.
However, much of the traffic will be identified as an application, even if it is as broad as ‘ssl’, and these applications are typically allowed across the firewall. The first step is therefore to identify the specific traffic that is being blocked, and this can be done easily from the NGFW traffic log, via the Monitor tab. Adding additional columns, such as ‘To Port’ can help identify the traffic later.
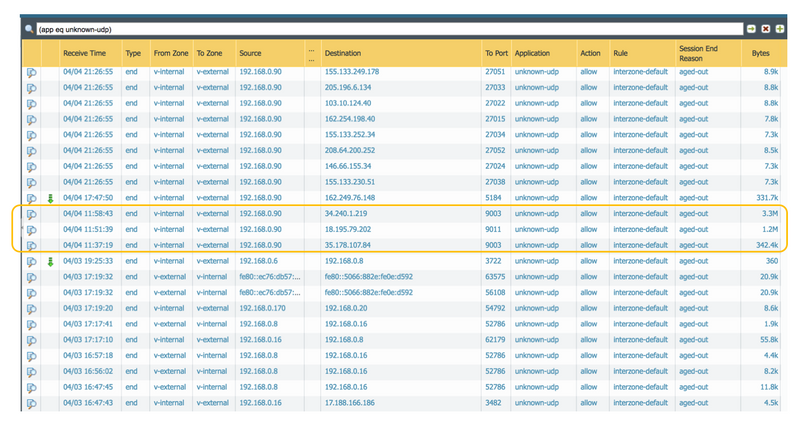 Identifying session in the traffic logCollect Traffic Samples from multiple clients
Identifying session in the traffic logCollect Traffic Samples from multiple clients
It is necessary to collect packet captures from multiple clients in order to find the correct signatures within that traffic. The packet captures can either be performed locally on the client, via Wireshark, or by using the firewall. To eliminate patterns that are related to users, or machines, it is necessary to collect a wide range of packet captures, from different machines, and with different user accounts. This ensures that only signatures relevant to the game are identified.
Analyse packet captures, and export relevant traffic streams
Once the packet captures have been collected, the relevant traffic streams can be identified and exported, using Wireshark’s ‘Follow TCP Stream’ and ‘Follow UDP Stream’ features.
For each packet capture, use the Firewall monitor output to understand the nature of the stream in question, for example, UDP port 9011, and use the Wireshark filter to find that traffic.
Using Wireshark to identify the Fortnite UDP Stream
Right click a packet in that stream, and select Follow > UDP Stream. Select ‘Show and save data as Hex Dump’, and then click Save as… to output data to a text file.
Wireshark - Follow UDP Stream
Repeat this step for each packet capture.
Find Similar data patterns in each stream output
Now that a variety of data stream samples have been created, these streams can be compared to find the identical patterns. A command like dwdiff is useful here. Unlike other diff tools, that rely on matching lines of data, dwdiff works by matching data at the word level. Dwdiff is a command that runs within the BASH shell. It is also available for Mac devices as per these instructions (similar results should be possible with the wdiff command, available for Windows). Using the command in the following way will create a new file containing the matching strings…
dwdiff -12 stream1.txt stream2.txt > diff1.txt
The output of this command can then be run against further streams to further fine tune the similar patterns…
dwdiff -12 diff1.txt stream3.txt > diff2.txt
The resulting file will show any patterns that matched across all of the streams.
Output from dwdiff command showing signature
Add signature to Custom App-ID
Any resulting hex arrays longer than 7-bytes can be added to a custom App-ID via the NGFW interface. To create a new App-ID, log into the NGFW, and navigate to Objects > Applications > Add. Alternatively, select an existing custom App-ID that you wish to update.
Configure characteristics of the Application in the Configuration and Advanced tabs. Then, under Signatures, add a new signature to the application. Create a new Condition, select ‘Pattern match’ as Operator, select the correct context, and input the hex pattern found, surrounded by /x parameters.
Creating a custom App-ID Signature
Once all Signatures are added, Commit the firewall configuration and test. If the signature has worked, the previously unknown traffic should resolve to the name of the custom App-ID. Policy can then be configured to define how and when the game should be allowed (ie, boarding houses after school hours). Finally, test the game to verify that the firewall correctly identifies the application.
Updates
Whilst testing the App Signature, a new version of the Fortnite client was released, and after this update, the App-ID signature failed to identify the traffic. To resolve, we repeated the steps above with the new client, and found that the signature found previously changed (although the new signature was consistent across all devices running the new client.)
Conclusion
A signature based approach is the most effective way of positively identifying application traffic, and where unpredictable ports and IP addresses are used by applications, it can be the only way. Palo Alto Networks’ Next Generation Firewalls provide the ability to create custom ‘App-IDs’, using signatures found in the application traffic streams. For organisations that use bespoke or unusual applications, App-ID is an effective way to allow such applications whilst enforcing a zero-trust approach to network traffic.