What is a Host Information Profile (HIP)?
The GlobalProtect Host Information Profile (HIP) feature can be used to collect information about the security status of the endpoints -- such as whether they have the latest security patches and antivirus definitions installed, whether they have disk encryption enabled, or whether it is running specific software you require within your organization, including custom applications. This information can then be used in security policies to decide if the endpoint is allowed to access a specific resource or not.
Settings for configuring HIP checks
This document provides an overview of the various settings available for configuring HIP checks for patch management and how these settings work together to determine the status of a HIP check for patch management. For more details on Host Information Profile and how that can be used in Security Policy Enforcement refer to Use Host Information in Policy Enforcement
Configuration 1
When a HIP object is configured with severity of None and no patches are listed, then any endpoint that reports at least one missing patch in the HIP report will match the HIP object in Figure 1.
Figure 1 (GUI: Objects > HIP Objects > (name))
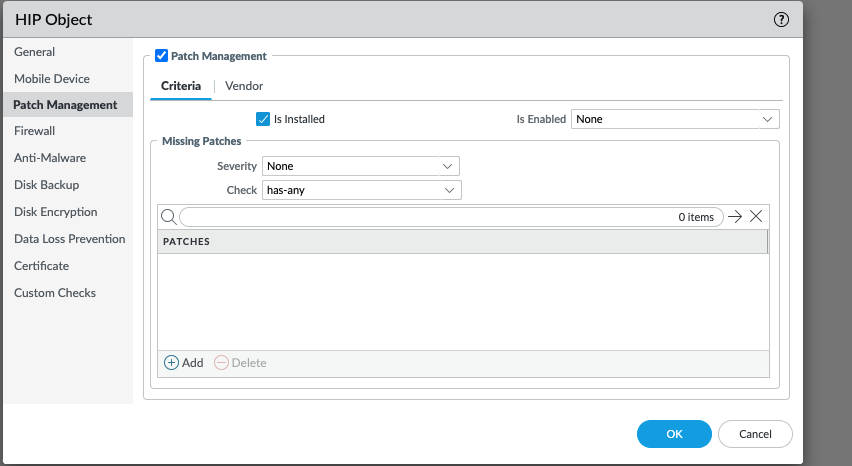
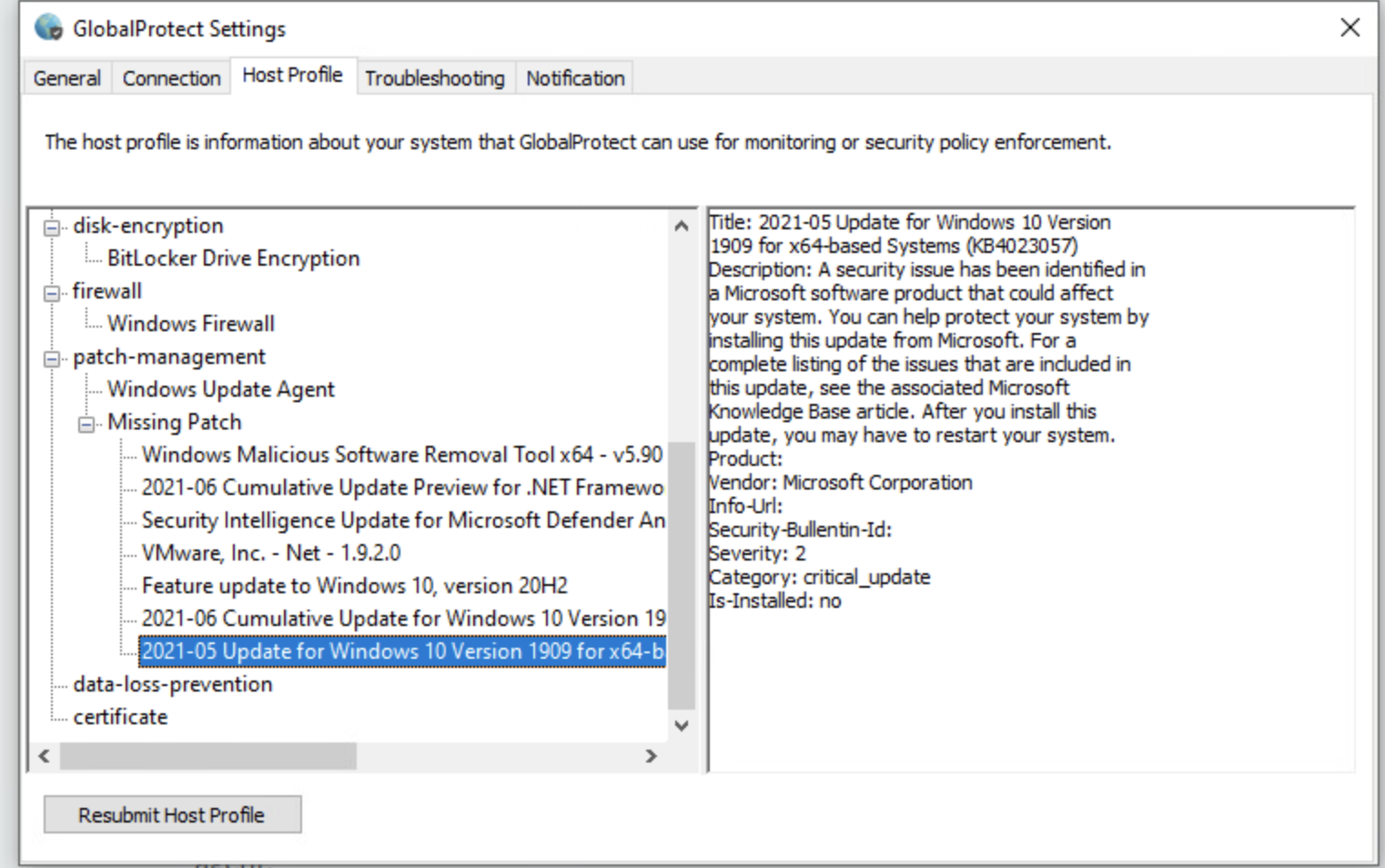
With this configuration, the severity of the missing patch does not impact the results. Also, the Check value (has-any, has-none, or has-all) does not impact the results. For example, an endpoint with the host state in Figure 2 will match this HIP object because this endpoint has at least one patch missing.
Figure 2 (GlobalProtect client icon > Settings > Host Profile)
Configuration 2
When a HIP object is configured with any severity value (besides None) and no patches are listed, then any endpoint that reports at least one missing patch that matches that severity will match this HIP object. See Figure 3.
Figure 3 (GUI: Objects > HIP Objects > (name))
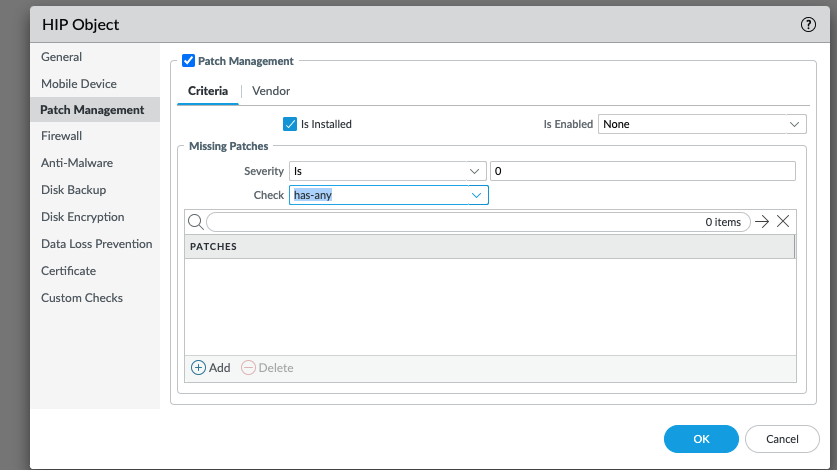
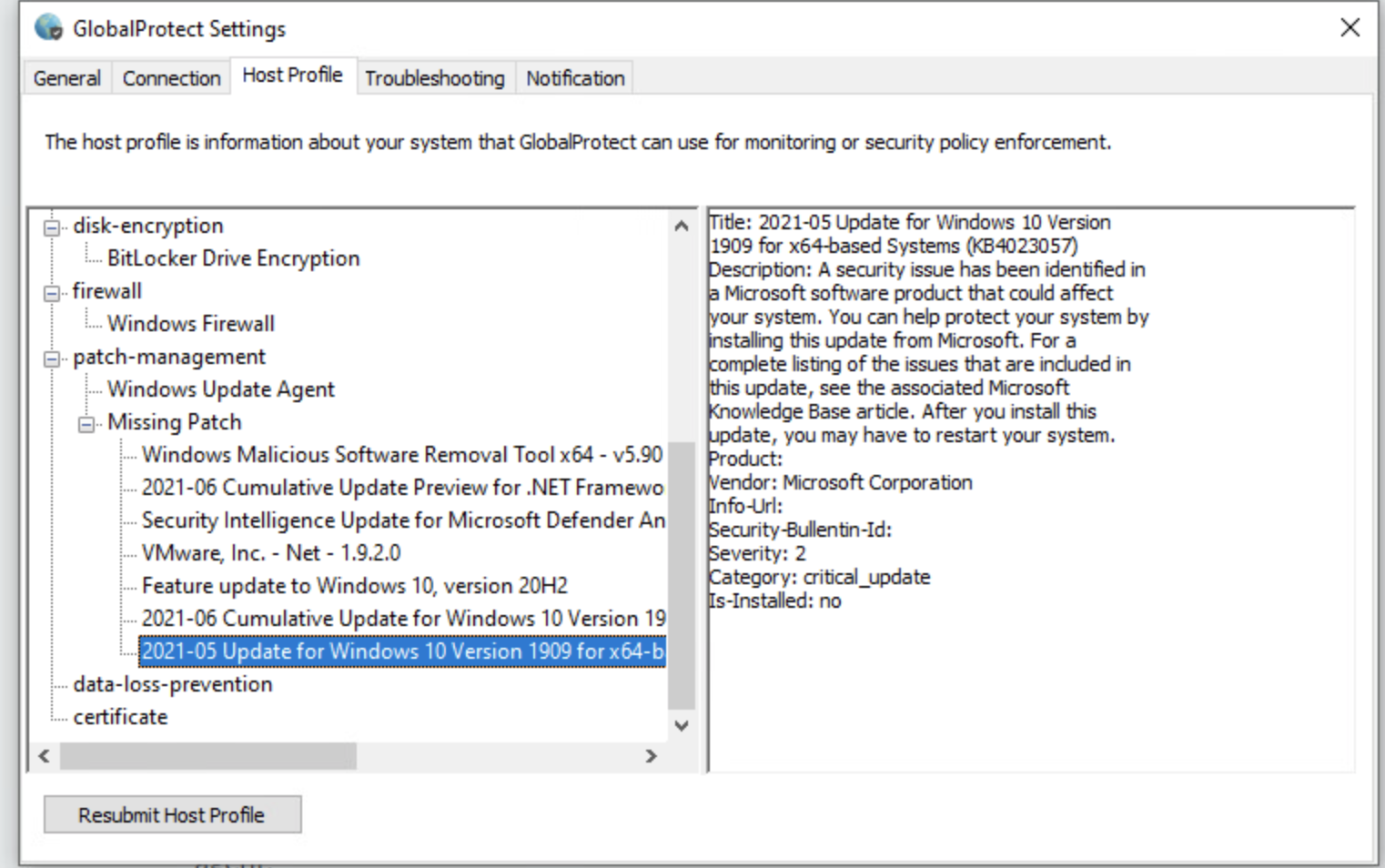
With this configuration, the severity of the patch that is missing does impact the result. (The severity should match the severity defined in the HIP object). However, the Check value (has-any, has-none, or has-all) does not impact the results. For example, an endpoint with the host state shown in Figure 4 will match this HIP object. We can tell this without looking at the severity of other missing patches on the endpoint because the patch highlighted in Figure 4 has severity 0 and it matches the HIP object definition.
Figure 4 (GlobalProtect client icon > Settings > Host Profile)
Configuration 3a
When a HIP object is configured with the following:
- Any severity value (besides None)
- The Check value is has-any
- The patch IDs are listed as shown in Figure 5.
Figure 5 (GUI: Objects > HIP Objects > (name))
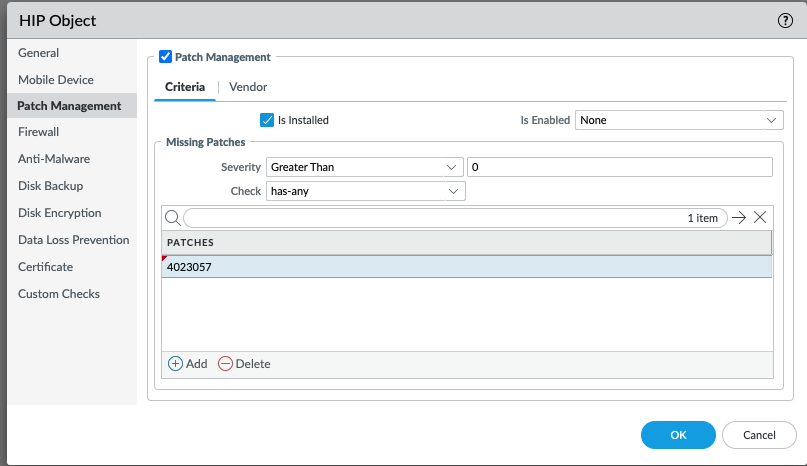
Then, an endpoint with at least one missing patch that matches the severity and also misses any of the patches listed, will match this HIP object.
Because the severity is set and patch IDs are listed, the Check value (has-any, has-none, or has-all) does have an effect. When the Check value is has-any, there is a match if both of these conditions are met:
- At least one missing patch on the client matches the severity
- Any of the missing patches configured for the firewall matches a missing patch reported by the client.
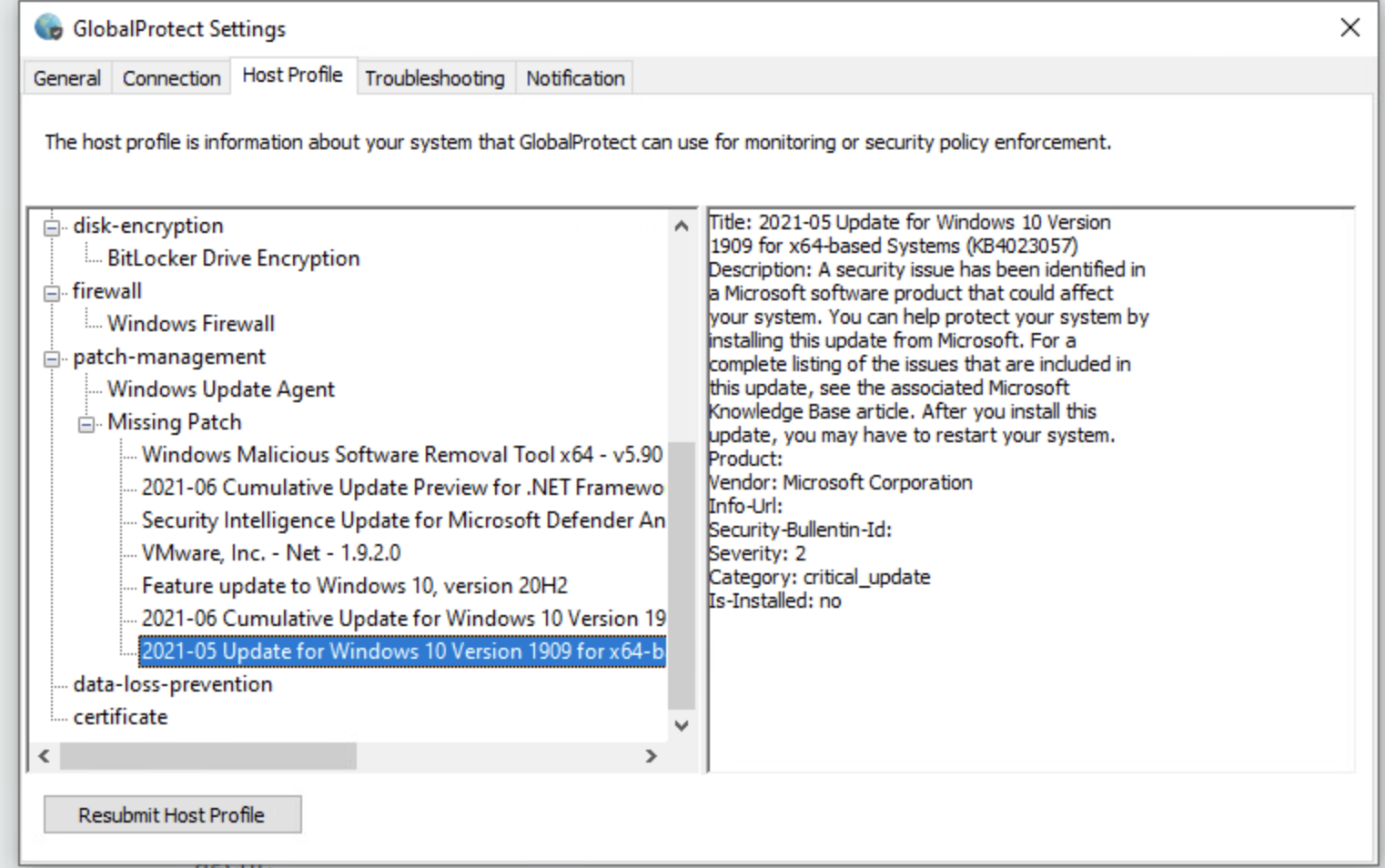
For example, an endpoint with the host state in Figure 6 will match this HIP object. This endpoint has at least one patch whose severity is Greater Than 0 and the endpoint is also missing one of the patches listed (KB4023057).
(If you want to add patch"KB4023057" to the list, you need to skip "KB" and register "4023057".)
Figure 6 (GlobalProtect client icon > Settings > Host Profile)
![]()
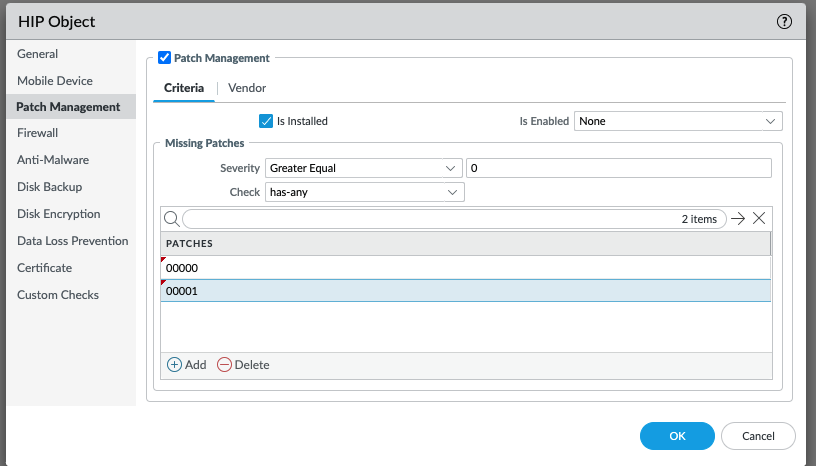
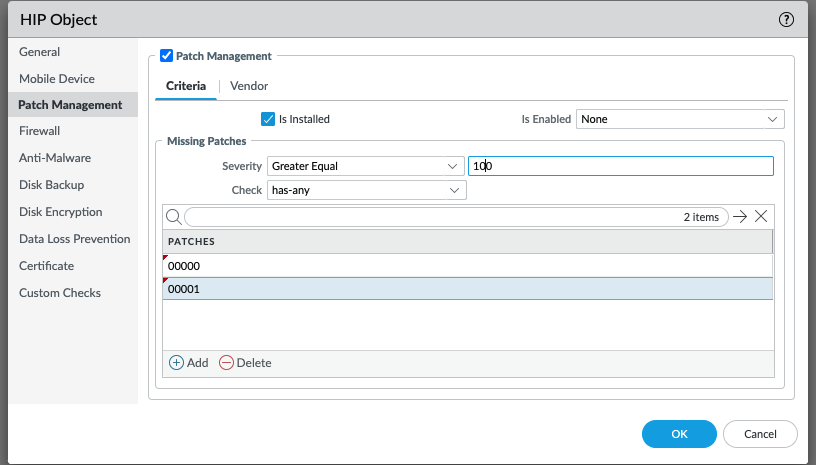
The same endpoint will NOT match the HIP object in Figure 7. Even though the endpoint is missing at least one patch of with a severity of Greater Equal to 0, it is not missing any of the patches listed (KB00000 and KB00001).
Figure 7 (GUI: Objects > HIP Objects > (name))
Configuration 3b
When the Check value is has-all, there is a match if both of these conditions are met:
- All the missing patches on the endpoint match the severity.
- All the missing patches configured on the firewall are included in the missing patches reported by the endpoint.
Configuration 3c
When a HIP object is configured with the following:
- Any severity value (besides None).
- The Check value is has-none.
- The patch IDs are listed as shown in Figure 8.
Figure 8 (GUI: Objects > HIP Objects > (name))
Then, any endpoint that meets both of the following conditions will match the HIP object:
- The endpoint does not miss any patch that matches the severity.
- The endpoint does not miss any of the patches listed.
With this configuration, when the severity is set and the patch IDs are listed, then the Check value (has-any, has-none, has-all) does have an effect.
When the Check value is has-none, there is a match if both of the following conditions are met:
- None of the patches missing on the endpoint match the severity.
- None of the patches listed in the firewall are included in the missing patches reported by the endpoint.
Conclusion
- Basically, there are two kinds of evaluations done on the missing patches reported by the GlobalProtect client. The match fails if either of the evaluations fail.
- Severity --This condition is applied to the list of patches missing on the endpoint. Check (has-all, has-any, has-none) -- This condition is applied against the patches listed in the HIP object.