Kerberos SSO: Kerberos Authentication for Admin access Keytab generation is used to supply the windows credentials automatically to the login prompt when a user accesses the WebGUI of the firewall. A network that supports Kerberos SSO prompts a user to log in only for initial access to the network (for example, logging in to Microsoft Windows). After this initial login, the user can access any browser-based service in the network (for example, the firewall web interface) without having to log in again, until the SSO session expires. (Your Kerberos administrator sets the duration of SSO sessions.)
You enable SSO for a Palo Alto Networks device by importing a Kerberos keytab into an authentication profile. A keytab is a file that contains Kerberos account information (principal name and hashed password) for the device, which is required for SSO authentication. Each authentication profile can have one keytab. If SSO authentication fails, the device prompts the user to log in manually and performs authentication of the type specified in the profile (for example, RADIUS).
ISSUE:
Kerberos SSO Admin authentication. Generation of keytabs for SSO and Active Directory settings
For customers who want to use Kerberos SSO authentication for their environment.
SYMPTOMS:
Authentication failing due to a malformed keytab.
RESOLUTION:
Here is a step-by-step procedure for generation of the keytab and the prerequisites:
- Service account on the domain controller which will carry the credentials.
For the service account, you need to enable AES 128 bit encryption / AES 256 bit encryption if the encryption algorithm is AES 128/256.
To enable the above settings, open the user account and click on Account, you will observe the encryption algorithm under Account options.
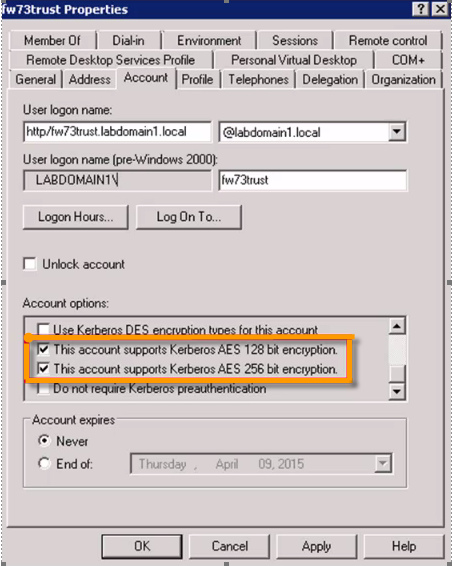 Service account settings
Service account settings
- Some settings under the browser.
For IE, the settings can be found under the below hierarchy:
Internet options> Security> Local intranet (sites button) > Advanced> add service FQDN to the list.
Here under websites, add the firewall’s fqdn or you can use *.domain.local.
Please note: Chrome will use IE settings.
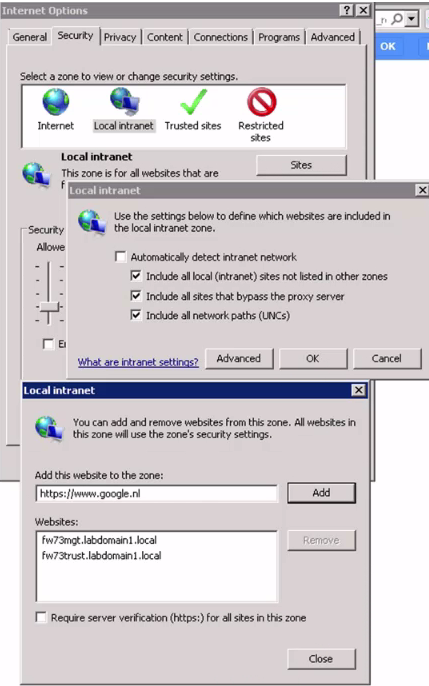 IE settings
IE settings
For firefox, type about:config as URL and search trusted URLs.
Enter the service FQDN in the value.
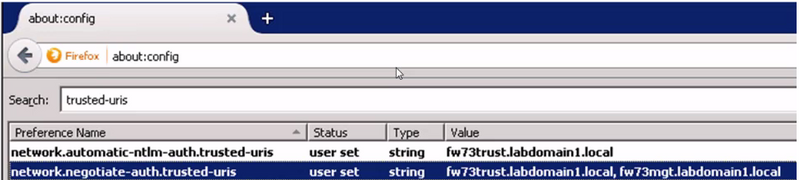 Firefox settings
Firefox settings
- Here is a command that can be used to identify the encryption algorithm on the Domain controller:
1. klist Command:
C:\Users\admin> klist
Client: gpdomuser1 @ GPQA.LOCAL
Server: HTTP/keytabgpgw61.gpqa.local @ GPQA.LOCAL
KerbTicket Encryption Type: AES-256-CTS-HMAC-SHA1-96 <- Information regarding the encryption algorythm.
Ticket Flags 0x40a50000 -> forwardable renewable pre_authentok_as_delegate name_canonicalize
Start Time: 10/1/2015 13:11:33 (local)
End Time: 10/1/2015 23:09:18 (local)
Renew Time: 10/8/2015 13:09:18 (local)
Session Key Type: RSADSI RC4-HMAC(NT)
Cache Flags: 0
Kdc Called: thirugpwinad.gpqa.local
2. setspn Command:
setspn -s http/fqdn domain\service account
For example
setspn -s http/fwtrust12.abc.local abc.local\service_account_username
3. The command for creating of the keytab is as follows:
ktpass -princ http/fwtrust12.abc.local@ABC.LOCAL -mapuser service_account_username -pass acct_password -crypto aes256-sha1 -ptype KRB5_NT_PRINCIPAL -out c:\temp\xyz-test.keytab -mapop set