This week’s Tips & Tricks discusses how to use the Threat Database, look at the threat logs and search for CVE numbers. If you're new to the Threat Logs inside the Palo Alto Networks WebGUI, we'll show you the many ways to get more details about those threats from the:
We will also talk about what CVE is.
Threat Logs
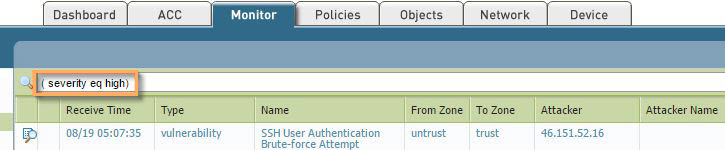
Let's start with the Threat Logs, which can be found inside the WebGUI > Monitor > Threat tab. Inside the threat logs, you'll see events that range from informational to critical in severity. See the example below, where we'll use an event High Severity as an example.
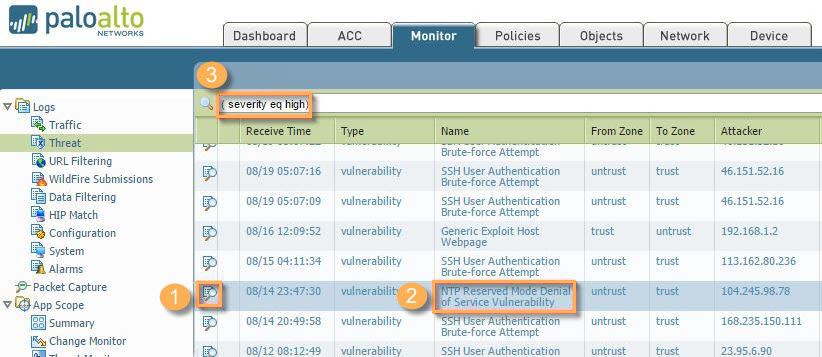
- First, click the magnifying glass in the first column of the logs to show the Detailed Log View, just like in traffic logs. This view shows you the Threat Details. Inside the Threat Details, you'll see the Threat Type, the Threat Name, the Threat ID, Severity, Repeat Count, URL, and Pcap ID. Please record the Threat ID to obtain more information later (33273).
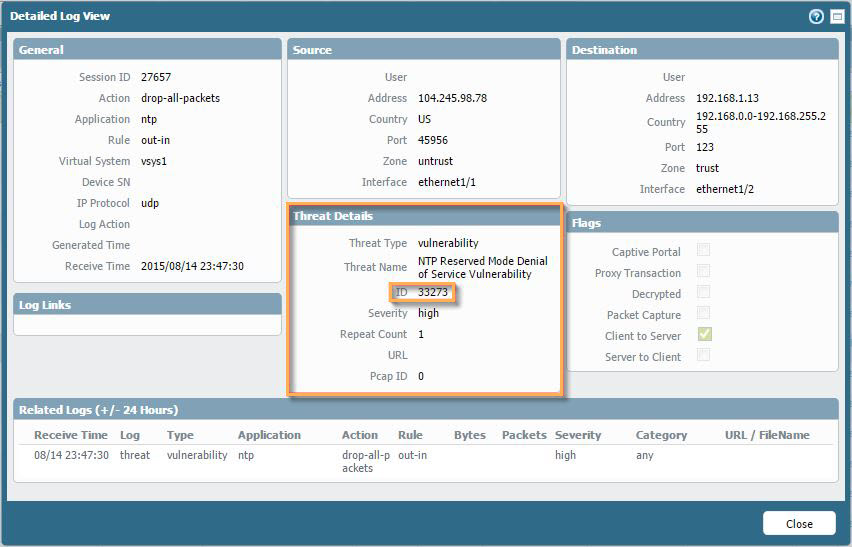
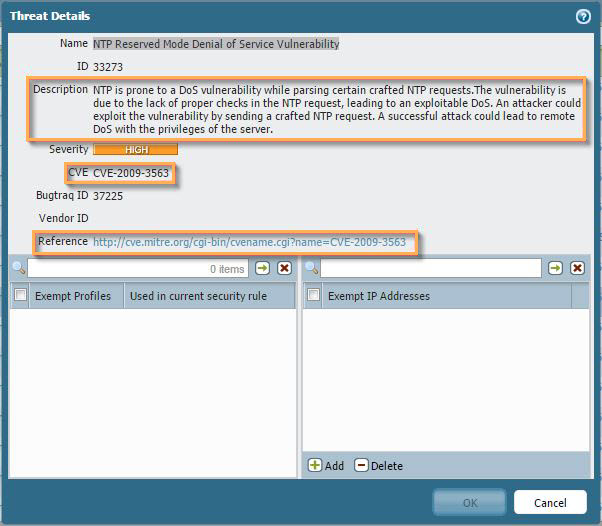
- Next, click on is the name of the threat itself. In this example, it's NTP Reserved Mode Denial of Service Vulnerability. This shows the Threat Details popup, which shows even more information, including: Name, Threat ID, Description, Severity, CVE number, Bugtraq ID, Vendor ID (if any), and Reference HTML link to the CVE info. You can also exempt Security Profiles or IP addresses in the lower part of the window.
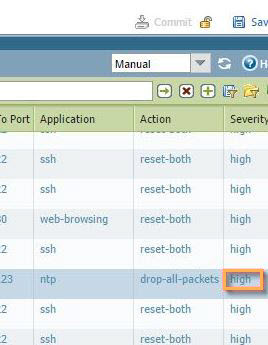
- Finally, you can filter out specific entries, as the logs tend to show informational and low threat logs, by default. To filter, first click on the severity, and in the search window at the top of the screen, change the severity level to what you'd like to see. In the example, we changed the level to (severity eq high) to filter out 'high' severity events. The 5 levels of severity are informational, low, medium, high, and critical.
Threat Vault
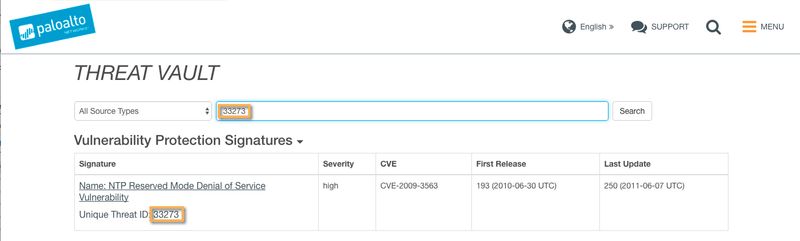
Alternatively, you have the ability to see all the same information about a specific threat if you visit: https://threatvault.paloaltonetworks.com and search on the Threat ID, name or CVE number. Using the example from earlier, you can search on 33273 (or use the CVE number to search).
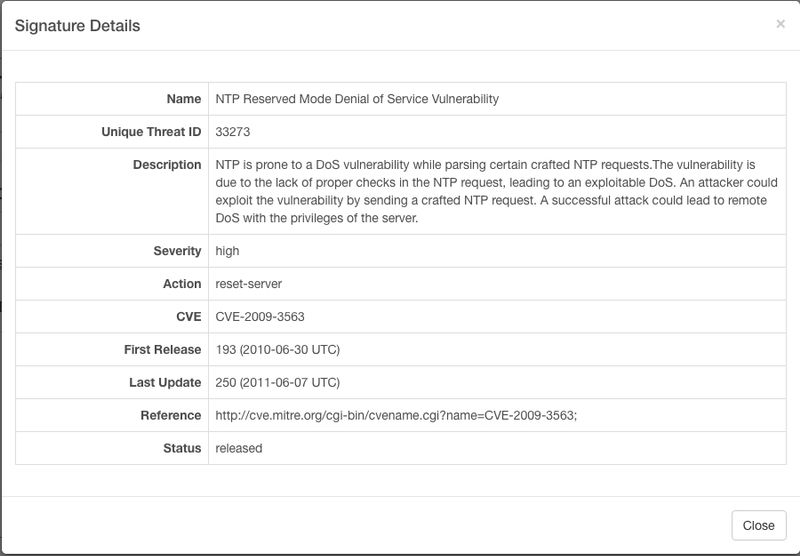
Click on the Signature Name to open the Signature Details, which shows the following: Description, References, Severity, Category, Default Action, First release and latest update, and CVE number.
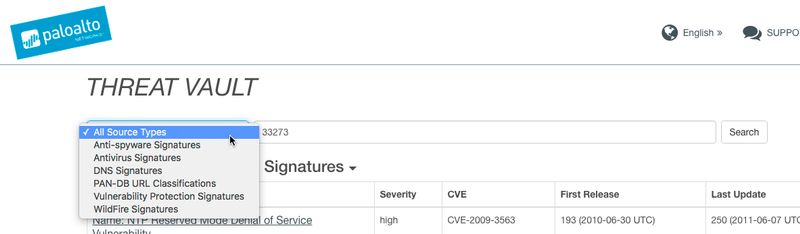
Note: While searching inside of the Threat Vault, you have the ability to search within "Types". By default, the search will cover all types but you also narrow down to "Anti-spyware" or "Antivirus Signatures" and several others to search inside of the Threat Vault.
CVE
The Common Vulnerability and Exposures (CVE) database provides unique common identifiers (called CVE-IDs, CVE-names, or CVE-numbers) for known information security vulnerabilities that can be used by the security industry as a standard for identifying vulnerabilities. Each CVE Identifier on the CVE list includes a CVE number, a brief description of the security vulnerability or exposure, and any pertinent references.
See Also:
Tips & Tricks: Custom Vulnerability
How to create a vulnerability exception
Video Tutorial: Custom Vulnerability
I hope this helps you get more familiar with the Threat DB and how to use it.
As always, we welcome all feedback and comments below.
Stay secure,
Joe Delio