When considering a firewall system, most admins think about traffic coming from the LAN network going out to the internet or a DMZ area, and some connections coming from the internet to a web server or mail server in the company's data center. Connections to the firewall itself are usually considered only with regard to management.
In this week's Tips & Tricks, we'll take a look at what kind of traffic could be coming from the firewall and ways to make sure everything's running smoothly without compromising security.
Assuming all possible licences are applied to the firewall and all updates configured to be downloaded automatically:
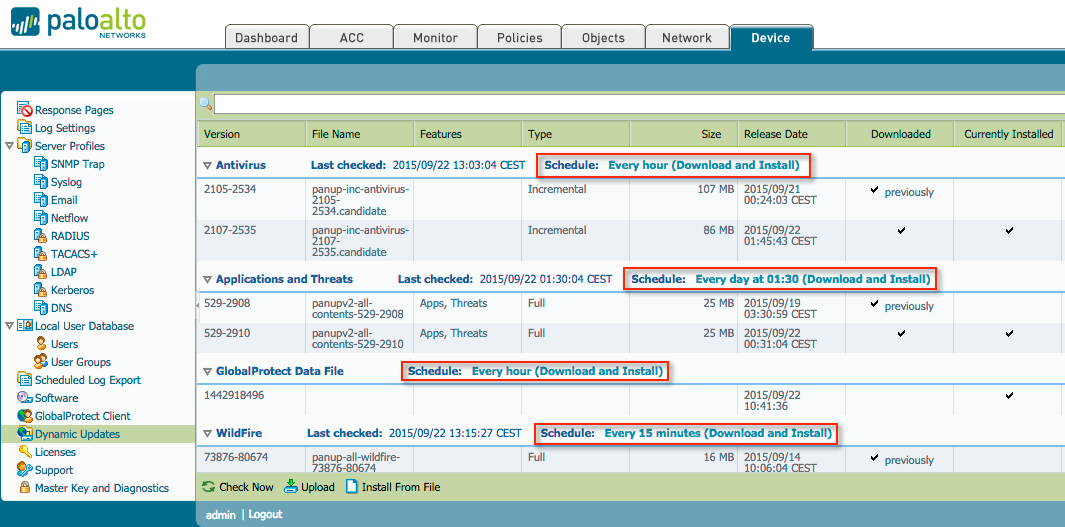
Several outbound connections originating from the management interface must be able to reach the internet. The firewall needs to download updates, get new AV signatures, check URLs for an appropriate category, and perform a host of other activities.
Outgoing connections will all be web-browsing and SSL sessions, destined for several different URLs, depending on the content being up- or downloaded.
- updates.paloaltonetworks.com and downloads.paloaltonetworks.com are used for AV , APP-ID, content and PAN-OS updates.
- prod.itpdownloads.paloaltonetworks.com is the newer site hosting dynamic updates.
- wildfire.paloaltonetworks.com is used for WildFire content updates and uploading files for analysis.
- urlcloud.paloaltonetworks.com and service.brightcloud.com are used for URL lookups and base-db download.
The above URLs, however, are the main URLs which redirect the firewall to a region-based subdomain (s0100.urlcloud.paloaltonetworks.com, eu-west-1.wildfire.paloaltonetworks.com and so on).
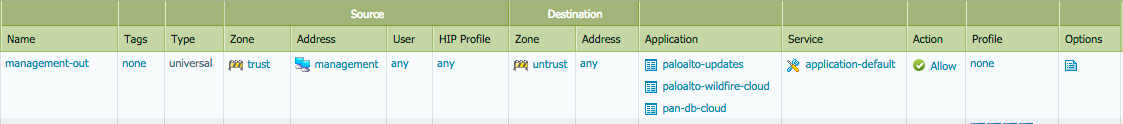
If you can collect a list of all the regional URLs appropriate to your device, you could enable a URL filtering profile to allow these connections, but this is fairly cumbersome, so we provided several applications to be used in a security policy to make things a little easier.
- pan-db-cloud allows outbound connections to all urls and suburls required to operate URL filtering.
- brightcloud allows the same functionality, if the BrightCloud URL filtering database is used.
- paloalto-updates allows retrieval of all apps, threats and content, PAN-OS updates, GlobalProtect software and updates.
- paloalto-wildfire-cloud allows download of WildFire content updates and upload of files to the cloud for inspection.
The applications enable a simple security policy, so all services can receive updates or files uploaded to the cloud for analysis, in the case of WildFire.
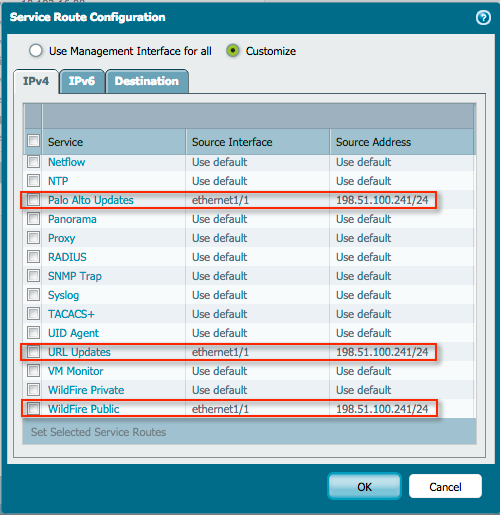
In some cases, the management interface may not be connected to the local LAN or be in an out of band network with no Internet access at all. To install vital updates onto the system without having the administrator perform these tasks manually, create a Service Route for each service.
A Service Route is an internal route from the management plane, traversing the internal backbone, onto the dataplane, where it can be bound to an internal or external interface. If a Service Route is bound to an internal interface, the above security policy can still be used to control and perform APP-ID on outbound connections, and if desired, do AV and content scanning as well.
If the Service Route is bound to the external interface, the services are allowed to connect to their respective Palo Alto Networks cloud services without requiring further configuration of the security policy. If the Service Route is bound to the external interface, the connection is simply allowed to connect to the Palo Alto Networks cloud services without requiring further configuration of the security policy.
I hope you enjoyed this week's Tips & Tricks. As always, comments and suggestions are welcomed in the section below.
Tom Piens