A virtual system (VSYS) is a separate, logical firewall instance within a single physical chassis. Enabling virtual systems on your firewall can help you logically separate physical networks from each other. Separate networks can come in very handy when specific networks should not be connected to each other. Using virtual systems (VSYS) also allows you to control which administrators can control certain parts of the network and firewall configuration.
In some cases, however, some connectivity needs to be enabled between VSYS. Rather than physically connecting the separate networks, which could cause a potential security breach, limited routing can be enabled to allow only specific subnets to communicate. Security policy can then be applied to prevent abuse of this bridge between networks.
Firstly, visibility has to be enabled between VSYS. Since a VSYS acts as a standalone system, it is not aware of any other VSYS residing on the same physical chassis.
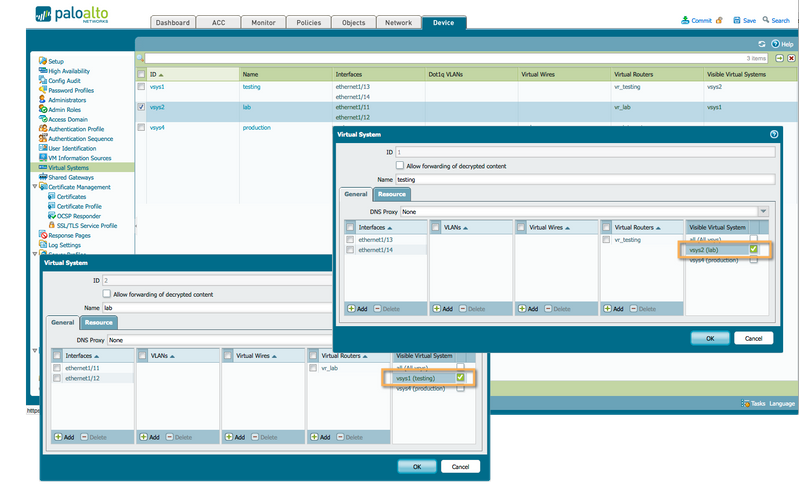
Next, a new type of zone, called 'External', needs to be created on each VSYS to allow sessions to traverse into a zone that connects VSYS. The External type will form a network of sorts that allows VSYS to communicate.
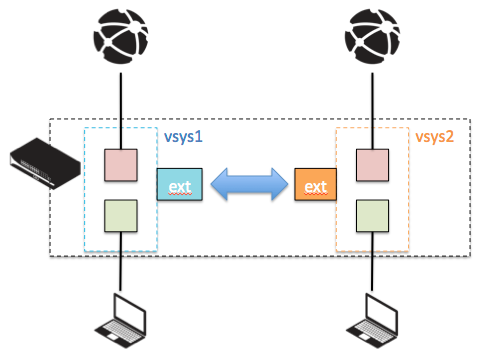
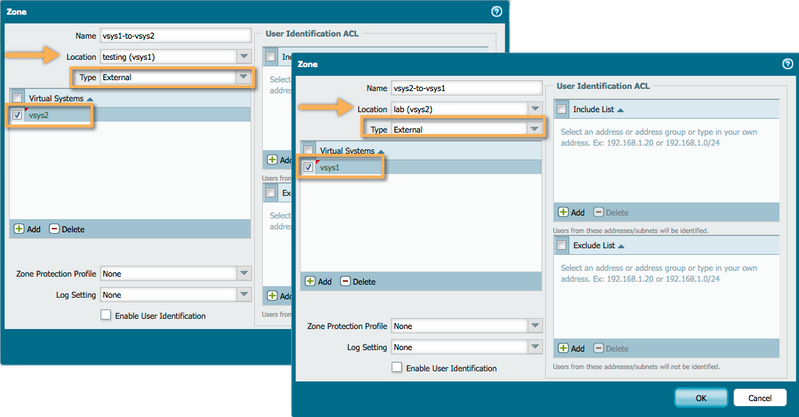
On each participating VSYS, create a zone with type 'External.' Add the destination Virtual System to allow this zone to represent the remote VSYS. Multiple destination VSYS can be added.
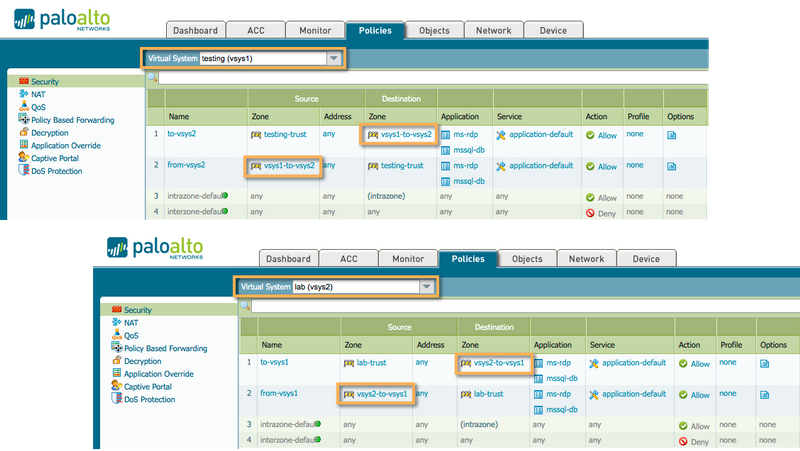
Each VSYS should then be configured with a security policy that allows the local zone to connect out to the External zone or from the External zone to the trusted network, if the connection is to be considered inbound. For example, in the case of an OOB network, the IT-VSYS can be allowed an outbound connection to the External zone, and the OOB VSYS could allow an inbound connection from the External zone.
Since the virtual routers are not aware of the subnets available in the remote VSYS, routing needs to be added to properly direct traffic to the External zone.
Configure each Virtual Router to be configured with routes for the appropriate remote subnets, with the next hop set to the remote VSYS' virtual router. In my example ,the 'testing' virtual router will need to be configured with a static route for the lab-trust subnet 10.6.0.0/24 pointing to the vr_lab virtual router, and a return route on the vr_lab virtual router, for testing-trust subnet 10.100.0.0/24 pointing to the vr_testing remote virtual router.
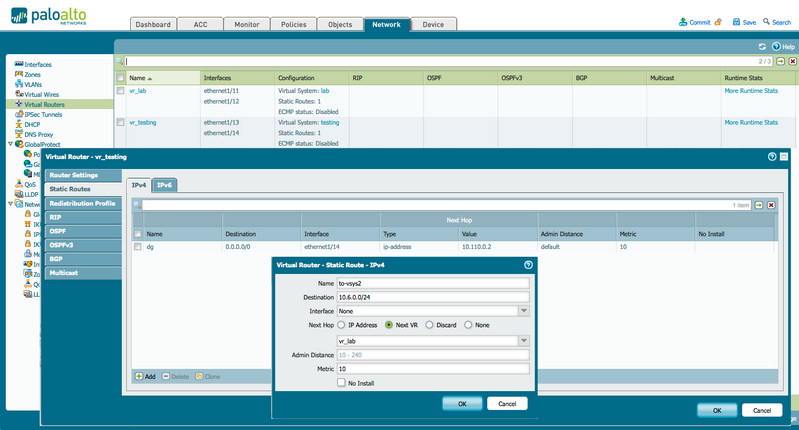

An inter-vsys route is not needed if both virtual systems are configured to use the same virtual router.
When this configuration is committed, clients located in the trust zones of both vsys1 and vsys2 will be able to connect to each other using the Microsoft Remote Desktop, or mssql applications per the security policy.