How to Export Threat PCAPs from CLI Using TFTP
Procedure
This documents briefly describes how to tftp export the threat-pcaps generated via threat profiles using the CLI. The emphasis on this document is on the syntax since if 'Tab' is used to autocomplete the command, the command will try to send the daily pcap directory rather than the files within via TFTP. This will cause an error on the server since TFTP is meant to send files and not directories.
To tftp export threat-pcaps:
> tftp export threat-pcap from 20120816
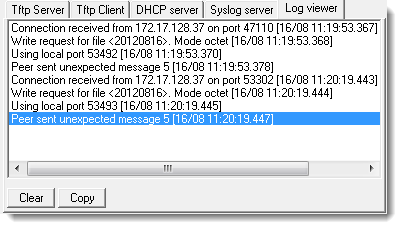
If Tab is used to autocomplete, the command will add the directory name to the command, which will cause the export to fail with an error on the server:
> tftp export threat-pcap from 20120816 to 172.17.10.39
mode set to octet
Connected to 172.17.10.39 (172.17.10.39), port 69
putting /opt/panlogs/session/pan/threat/20120816 to 172.17.10.39:20120816 [octet]
Error on TFTP server is seen per screenshot 'server_error.png' attached.
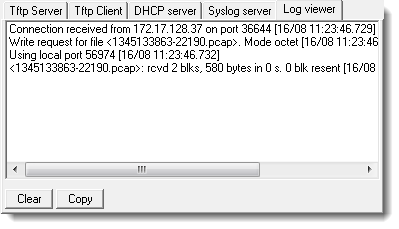
The correct syntax is to append a / or a /* at the end of the directory name so that the command will export the folder's contents and not the folder itself.
> tftp export threat-pcap from 20120816/ to 172.17.10.39
mode set to octet
Connected to 172.17.10.39 (172.17.10.39), port 69
putting /opt/panlogs/session/pan/threat/20120816/1345133863-22190.pcap to 172.17.10.39:1345133863-22190.pcap [octet]
Sent 580 bytes in 0.1 seconds [56365 bit/s]
owner: achitwadgi