Details
By connecting different sites to MPLS WANs, companies can provide convenient internal network connectivity between sites. Often, the MPLS routers deployed are connected to the internal network through the firewall, providing visibility and control for the traffic passing across the MPLS. How the Palo Alto Networks firewall is configured is an important aspect in determining what traffic is allowed to pass to or from the MPLS cloud. It is important to remember that the Palo Alto Networks firewalls are not MPLS routers, but can serve as a logical connection point to the MPLS cloud by being connected to the MPLS router that terminates MPLS at the site.
Example network topology:
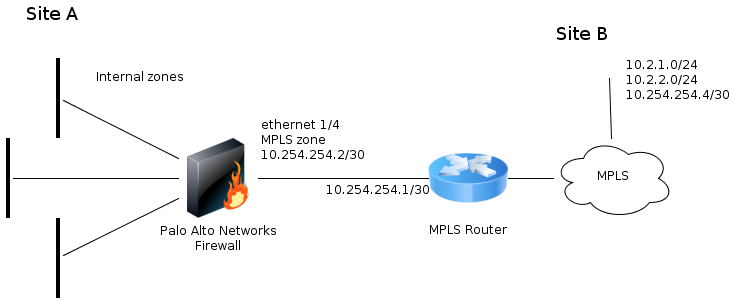
Recommendations
Zones
To control and monitor traffic passing across the MPLS cloud, it's important to assign the Ethernet interface connecting to the MPLS router to a different zone than the other interfaces. It will be easier to later define security policies which allow traffic to or from the MPLS zone and also to or from the other internal zones. In this scenario, traffic logs can be available for the security policies that are created between the zones. If the interface connecting to the MPLS cloud is in the same zone as the trust for example, then by default traffic between MPLS networks and trust networks will be allowed and not logged unless there's an explicit security policy denying traffic to and from the trust zone.

Routes
The firewall requires routes for every network at the sites across the MPLS. This can be accomplished by configuring static routes for those networks with the next hop IP address as the MPLS router's IP address. Another possibility is deploying dynamic routing on the routers at each site if there are many networks and many sites.

Security Policies
If full connectivity between the sites is necessary or desired in initial setup, then two allow policies can be created; one for the MPLS zone to reach the internal zones and one for the internal zones to reach the MPLS zone. Depending on what access is needed across the sites, then the security policies can be restricted to only allow what is necessary.

NAT Policies
No NAT policies need to be configured since typically there is no need to translate the private address ranges because the WAN enables private networks from one site to reach the private networks at the other site. If however there appears to be overlapping subnets at two sites then NAT can be employed to hide the addresses at one end by mapping them to a unique subnet. A similar technique is used with IPSEC VPN tunnels and that is documented in How to Use NAT in an IPSEC VPN Tunnel. The subnet whose addresses are mapped can only be accessed from that point using the mapped addresses, so keep in mind the implications for accessing servers and referencing any DNS records.
Note: Typically, the local MPLS router needs to have routes to reach the remote sites networks. Also, the remote site needs to have routes in place to reach the local site. If there is a firewall in place at the remote site, its policies will similarly need to allow the traffic through.
owner: astanton