How to Create an Application Filter to Block High-Risk Applications
Procedure
Overview
This document demonstrates how to create a security policy to deny high-risk (5) file-sharing applications that leverage peer-to-peer technology under the general internet category.
Steps
- Under the Policies Tab, select "Security" and then add a security rule.
- Enter the necessary information under the General, Source, User and Destination tabs, and select the "Application" tab.
- Select "Add." Scroll to the bottom of the drop-down and select "Application Filter."
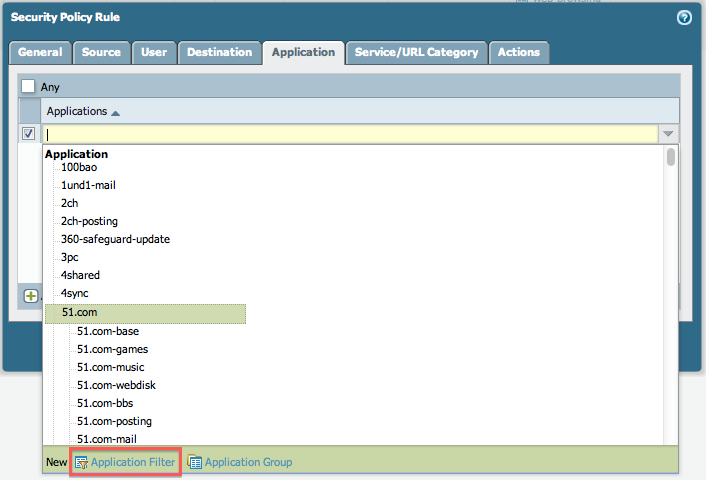
- Name the Application Filter that you want to create.
- Since we are interested in high-risk (5) file-sharing applications that use peer-to-peer technology, follow these instructions:
- Under Category column click to highlight general-internet
- Select file-sharing under Subcategory
- Technology will be peer-to-peer
- Risk is 5
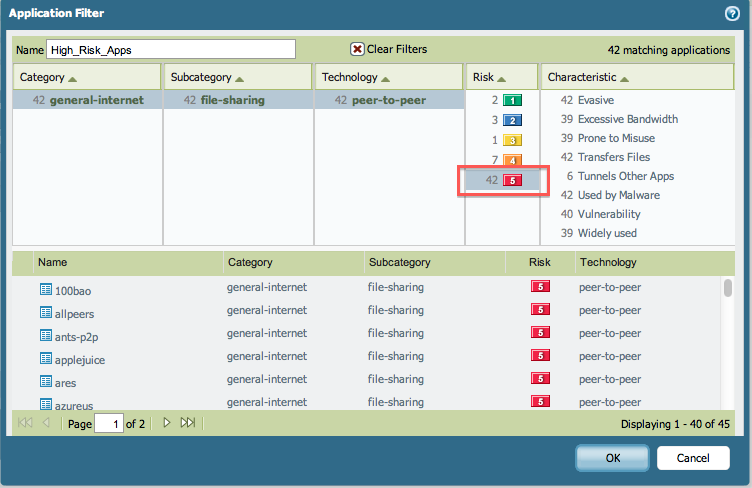
- Select "OK" to save. The Application Filter will appear in the rule.
- Complete the rest of the Security Policy rule. It is recommended to leave Service/Url Category as 'Any'. Action is then set to 'Deny'.
By following the above steps, traffic through the firewall will be categorized by the application filter.
Note: Application filters are dynamic. If a built-in category is chosen, a group can be made that is usable in rules. This will include everything that matches that category. As applications are re-categorized or as new ones are added to that category, they will be added or removed from the filter dynamically. This can potentially lead to issues because re-categorization can cause applications that were previously allowed to now be disallowed, and vice versa. With an application group, though, applications are being grouped in the same manner as a service-group or address-group. When more applications for allow or block are added, they will need to be added to the application group manually.
See Also
For an in-depth understanding of application dependencies in order to effectively apply the High-Risk Apps to a security policy, refer to the following document:
How to Check if an Application Needs to have Explicitly Allowed Dependency Apps
owner: sodhegba