Details
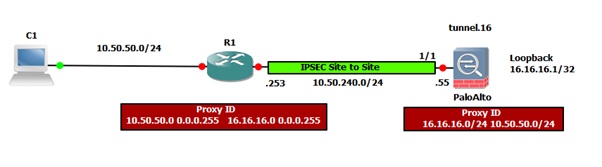
The following diagram illustrates an IPSec site-to-site between a Palo Alto Networks firewall and Cisco:
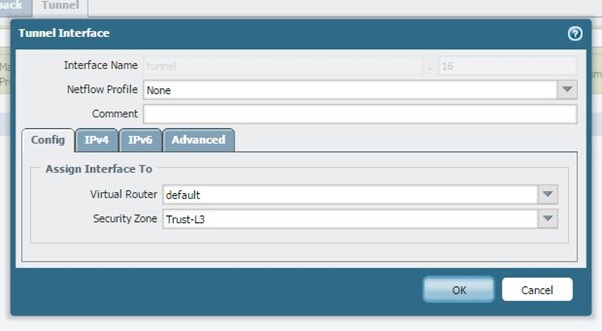
Tunnel Interface
Create a tunnel interface and select virtual router and security zone. The security policy needs to allow traffic from the LAN zone to the VPN zone, if placing the tunnel interface in some separate zone other than the internal LAN network zone.
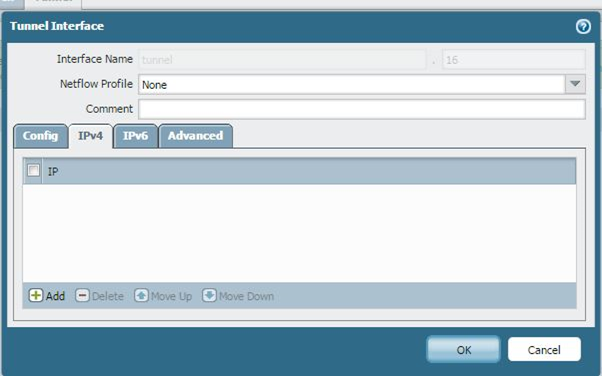
The IP address is not required. To run the routing protocol through the tunnel, you must add an IP address to the tunnel interface.
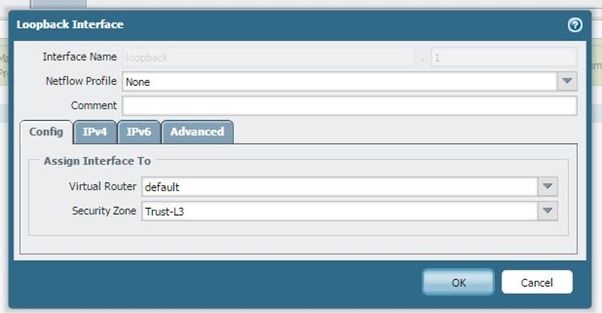
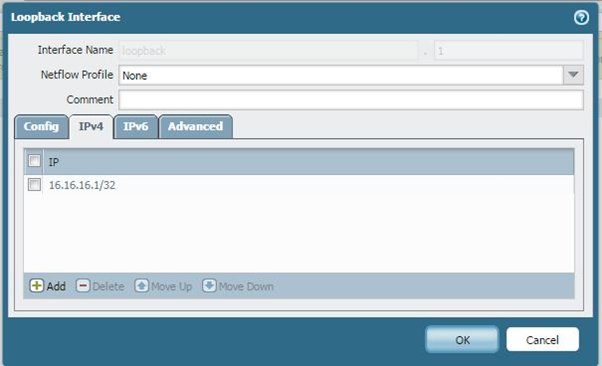
Loopback Interface
For this scenario we are using a Loopback interface to simulate a host in an internal zone for testing purposes, otherwise there is no need for the loopback interface.
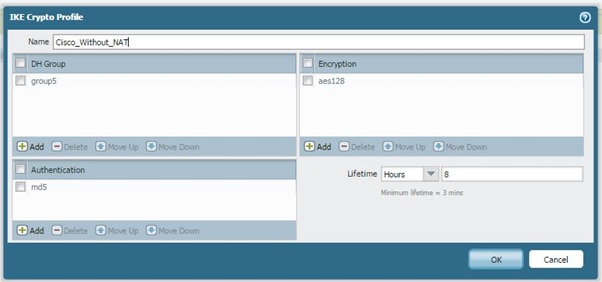
Phase 1
Create a Phase 1 policy, which will be the same on both sides:
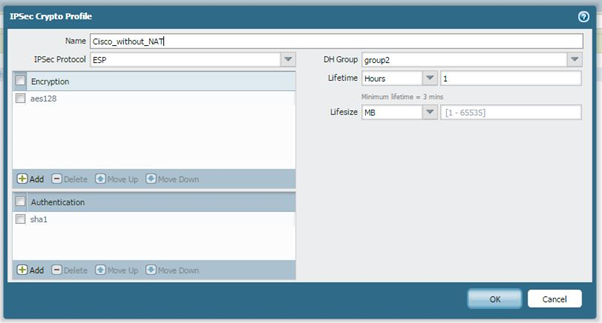
Phase 2
Create a Phase 2 policy, which will be the same on both sides:
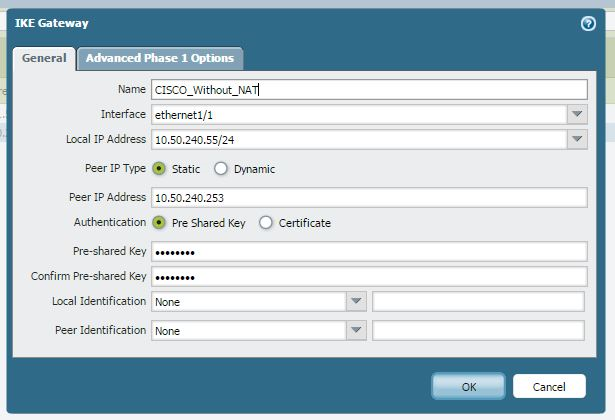
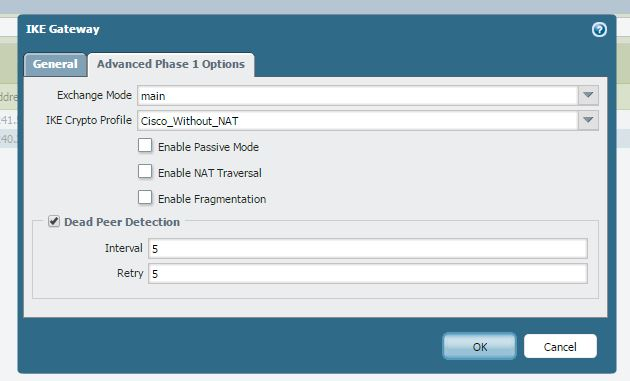
IKE Gateway
The peer IP address must be reachable through the interface Ethernet 1/1, as shown below:
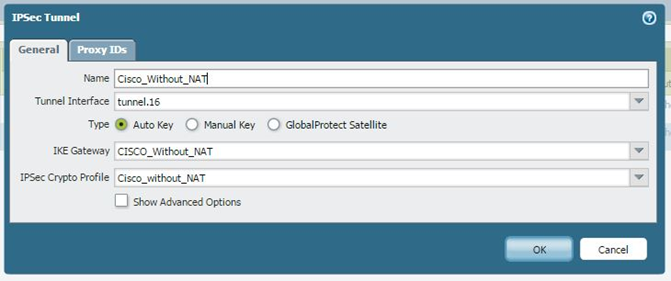
IPSec Tunnel
Select the tunnel interface, the IKE gateway, and the IPSec Crypto profile to make sure the Proxy-ID is added, otherwise phase 2 will not come up.
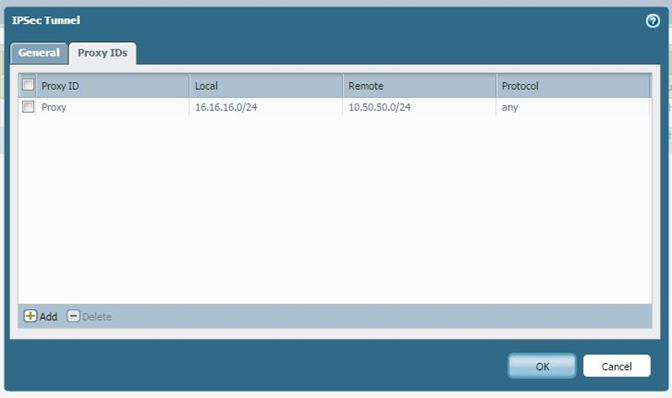
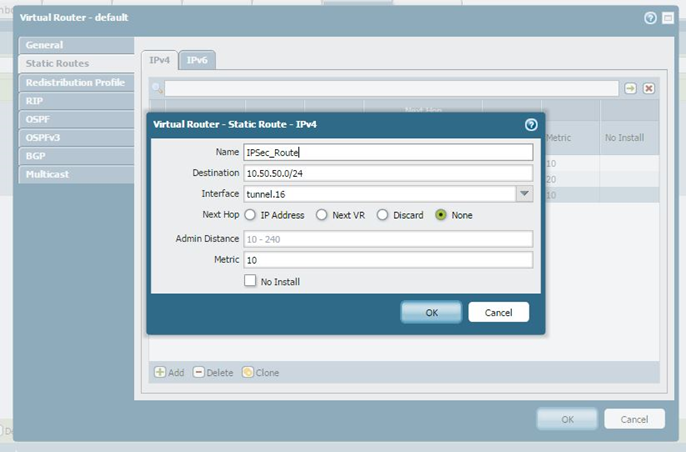
Route
Add the route of the internal network of the other side pointing towards the tunnel interface and select None:
Configuring Cisco
ip access-list extended Crypto_Acl
permit ip 10.50.50.0 0.0.0.255 16.16.16.0 0.0.0.255
crypto isakmp policy 16
encr aes
hash md5
authentication pre-share
group 5
crypto isakmp key cisco123 address 0.0.0.0 0.0.0.0
crypto ipsec transform-set TSET esp-aes esp-sha-hmac
crypto map CMAP 10 ipsec-isakmp
set peer 10.50.240.55
set transform-set TSET
match address Crypto_Acl
interface FastEthernet0/0
crypto map CMAP
owner: pakumar