Overview
This document explains how multiple rules for vulnerability and sypware profiles are processed for the same severity.
Details
If one vulnerability profile has multiple rules for the same severity then traffic takes the top down approach, much like security policies.
Examples
The following vulnerability profile has 3 rules:
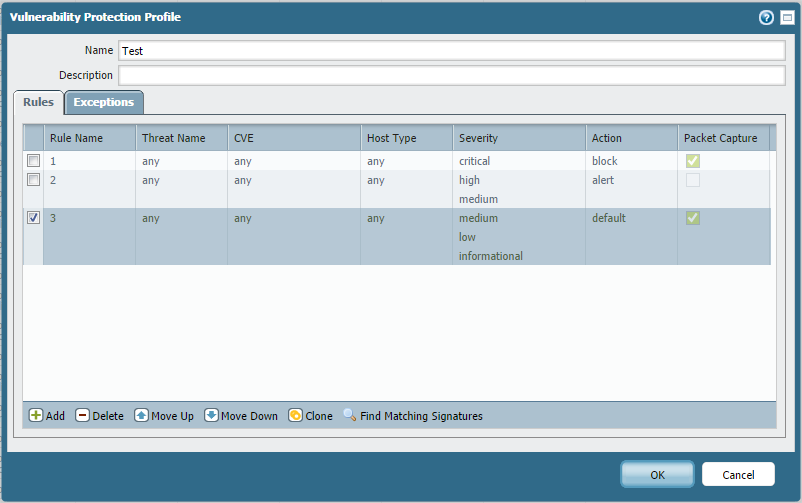
If the Palo Alto Networks firewall detects traffic with a MEDIUM severity vulnerability, rule 2 will take effect and an ALERT action will be applied.
The following spyware profile has 3 rules:
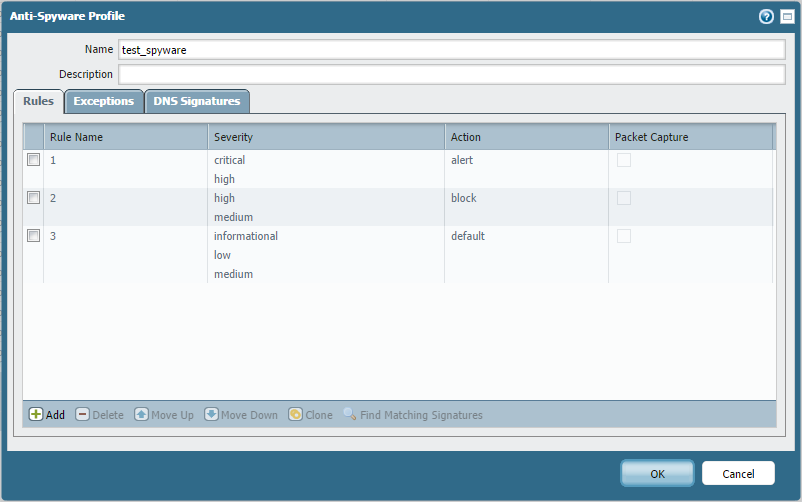
If the firewall detects traffic with a HIGH severity spyware, rule 1 will take effect and an action of ALERT will be applied.
For file blocking rule order precedence, refer to this document: File Blocking Rulebase and Action Precedence
owner: kadak