Find the Proper Bind Information
- To find the Bind DN, run the following command with the example username of test1 from the command line of the AD server:
- dsquery user -name test1
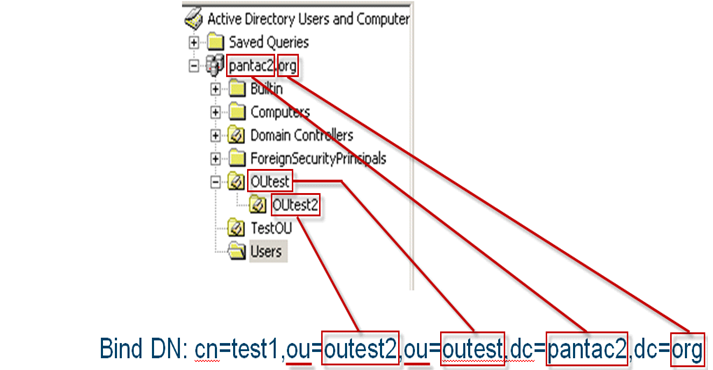
- should receive the Bind DN "CN=test1, OU=outest2, OU=outest, DC=pantac2, DC=org"
- Or one can use an LDAP browser to find the Bind DN:
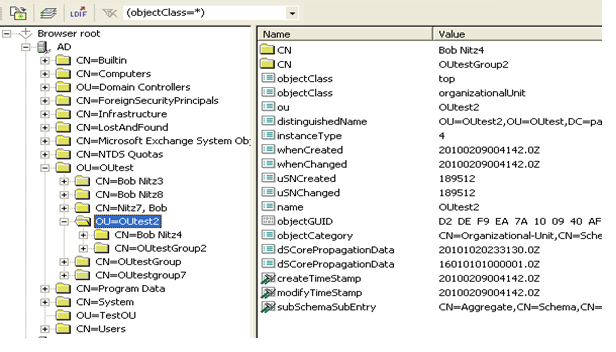
- The Base DN is where the PAN will start searching in the directory structure.
- The Bind DN is the username that will be used to do the searching and request the authentication.
Note: In Active Directory, a blank folder icon represent Containers (CN) while folders with icons are Organizational Units (OU).
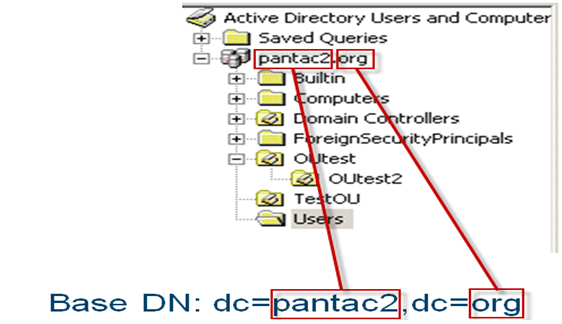
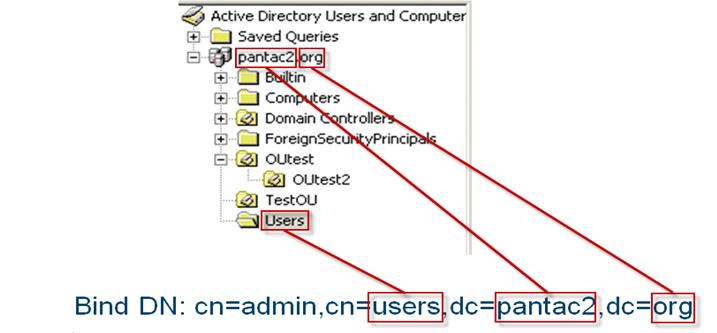
For example, if the admin account is in the user's container, the Bind DN information is
cn=admin,cn=users,dc=pantac2,dc=org
In the following example, the test1 account is in the OUtest2 Organizational Unit (OU), and OUtest2 is in OUtest.
Configure LDAP Server Profile.
- Device > Server Profile > LDAP
- TCP port 389 is the standard port for unencrypted LDAP, port 636 is used when Require SSL/TLS secured connection is selected.
- LDAP information
- Type: active-directory
- If the server list has been populated and the servers are reachable by the management interface, the Base DN will auto populate when you click the drop-down arrow
- Base DN: DC=pantac2, DC=org
- Bind DN supports UPN (ldap-auth@pantac2.org) and Distinguished Name (CN=ldap-auth,OU=Users,DC=pantac2,DC=org) formats
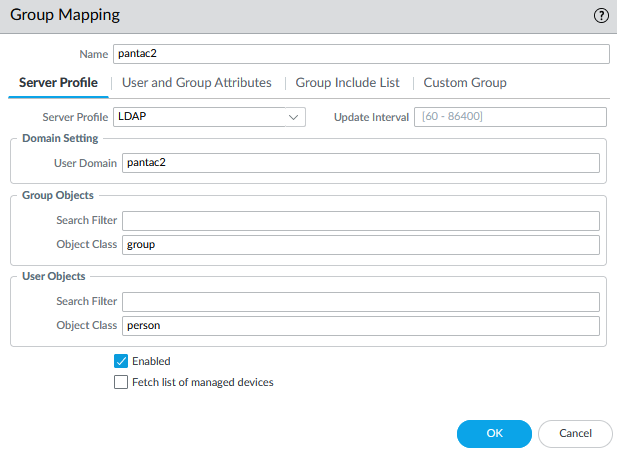
Configure Group-Mapping Settings.
Device tab > User Identification > Group Mapping Settings: make sure to set the User Domain
- Click the Group Include List Tab.
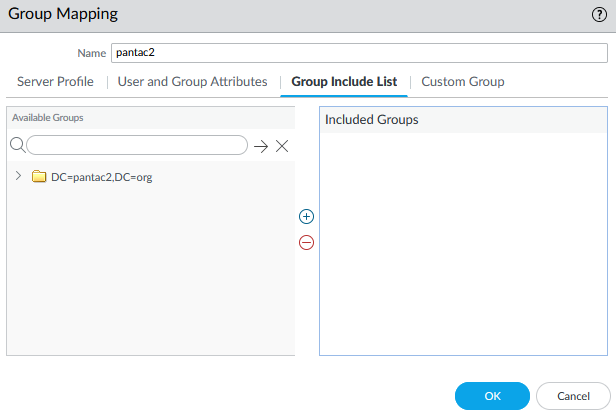
- Click the + sign next to the Base in the Left column to drop the list of available folders to search for the groups you want to Query for
- Click on the groups listed starting with the "cn=" that you want to have on the firewall to use in policies and click the + sign in the middle to add them to the included list of groups.
Warning! If there are no groups in the include list to the right, all groups in AD will be queried and may cause load issues.
- Commit.
- Verify the connection to the LDAP server with the following CLI command
> show user group list
Note: When multiple group-mappings are configured with same base dn or ldap server, each group-mapping must include non-overlapping groups i.e include group list must not have any common group.
Configure LDAP authentication in Device > Authentication Profile.
- Include any groups that you are querying for that will be used in the Authentication Profile
- This Profile can be used for Captive Portal, Global Protect, User log on, or any authentication through the firewall.
- You can create other Authentication profiles for different functions if the groups in the allow list will be different.
- If required, the input username can be modified to accommodate down-level or UPN username formats.