Starting from PAN-OS 8.0, we have an option to have a secure communication, with the help of certificates, between the firewall and the User-ID Agent.
NOTE: This requires the firewall to be on PAN-OS 8.0 (or later) as well as the User-ID agent to be on 8.0 (or later).
In this process, the UIA (User-ID Agent) will present a certificate to the firewall to validate. The firewall will check this certificate as per the certification profile configured. If it passes all the checks in the certificate profile, the firewall will accept the connection from the UIA. This can ensure safety against "rogue" UIAs.
Here's a step-by-setup walkthrough to configure this:
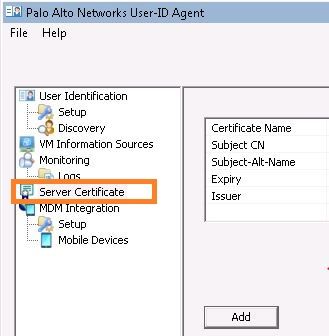
1. Launch the UIA, you should see a new option called 'Server Certificate':
2. We need to create a new CSR for the UIA and get it signed by either an external CA, in-house CA or a self-signed certificate present in the firewall. (Note: We will need the CA certificate to be present on the firewall so we can use it in the Certificate profile and validate the UIA's certificate). Please make sure we install the complete chain on the USERID agent as well.
3. Once we have a certificate, we can import it in the UIA along with its private key. Make sure to commit the configuration.
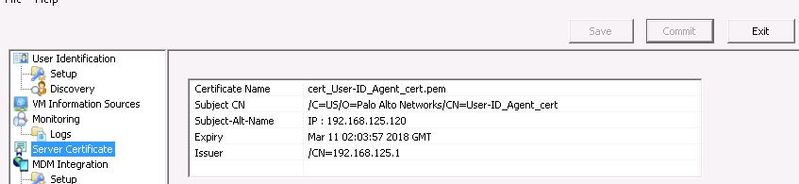
4. Create a new certificate profile and use the CA used to sign the UIA's CSR. (If using a self-signed certificate, use a common root CA)
5. You should see a new tab under Device >User Identification, called 'Connection Security':
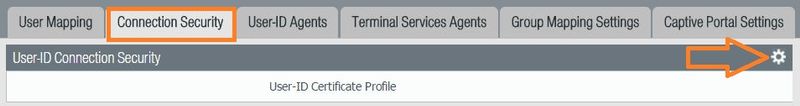
Choose the certificate profile created in step 4.
Alternatively, starting PAN-OS 10.0 assign the certificate profile on the firewall under Secure Client Communication:
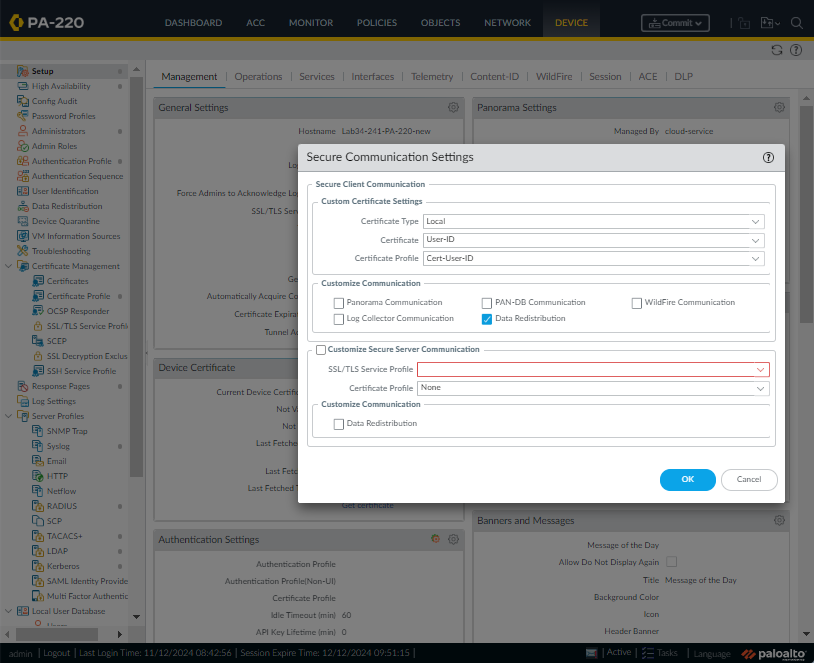
- Select DEVICE > Setup > Management > Secure Client Communication
- Under Certificate Type choose Local.
- Select the Certificate which will be presented to the server (UI-Agent) to secure outgoing connection from the firewall. (This can be left set to default which is None). (If a certificate is selected then the Root CA that signed the firewall’s custom certificate must be loaded into the Windows Trust store of the Windows machine where UID Agent is installed).
- Select the Certificate Profile configured in step 4. (This will be used for validating the server certificate while connecting to various peer services such as UI-Agent).
- Check Data Redistribution.
- Click OK.
- Commit.
-
Use the following CLI command to confirm the certificate profile (SSL config) uses Custom certificates: show redistribution agent state
<agent-name> (where
<agent-name> is the name of the redistribution agent or User-ID agent.
admin@10.0-New-CFW> show redistribution agent state 92-uid-Agent (10.0 Client FW)
Agent: 92-uid-Agent(vsys: vsys1) Host: 10.x.x.49(10.x.x.49):5007
Status : conn:idle
Version : 0x6
SSL config: : Custom certificates <<<<<
num of connection tried : 1
num of connection succeeded : 1
num of connection failed : 0
num of status msgs sent : 84
num of status reply msgs rcvd : 84
num of request of ip mapping msgs sent : 0
num of request of all ip mapping msgs sent : 1
num of user ip mapping msgs rcvd : 0
num of user_id_command msgs rcvd : 0
num of hip update msgs rcvd : 0
num of hip report get messages sent : 0
num of hip report get msgs rcvd : 0
num of iptag post msgs rcvd : 0
num of usertag post msgs rcvd : 0
Last heard(seconds ago) : 0
NOTE: In case a certificate profile is configured under both Device > User Identification > Connection Security and Device > Setup > Secure communications settings > Secure Client Communication (where Data Redistribution is selected)
The certificate profile configured in the latter will take precedence and will be used to validate the user-id agent certificate.
6. If the commit goes well, you should see the UIA connected successfully with the firewall.


Failure Scenario
If an incorrect or no certificate is present on the UIA while Connection Security is enabled on the firewall, you will see the following log entry in the System (and userid) logs:
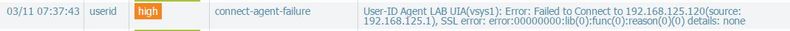
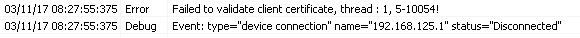
For the same failure, on the agent, you would see the following logs (under Monitoring->Logs):
Hope this helped. Stay safe!