Forwarding threat logs to a syslog server requires three steps
- Create a syslog server profile
- Configure the log-forwarding profile to select the threat logs to be forwarded to syslog server
- Use the log forwarding profile in the security rules
- Commit the changes
Note: Informational threat logs also include URL, Data Filtering and WildFire logs.
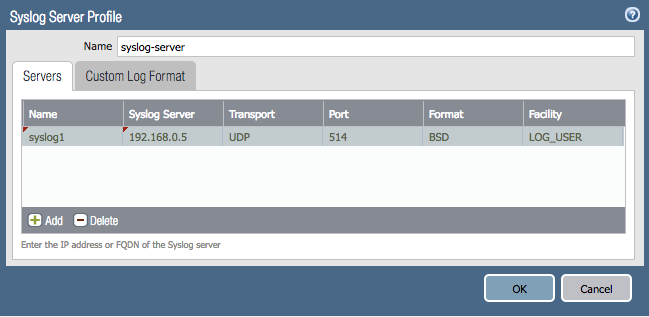
Syslog server profile
Go to Device > Server Profiles > Syslog
- Name: Name of the syslog server
- Server : Server IP address where the logs will be forwarded to
- Port: Default port 514
- Facility: To be elected from the drop down according to the requirements
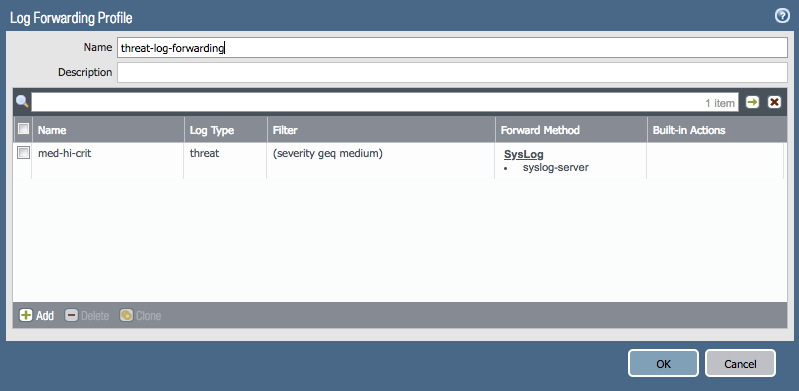
Log forwarding profile
Go to Objects > Log forwarding
Create the syslog server profile for forwarding threat logs to the configured server.
 Add a Log Forwarding Match List to the profile
Add a Log Forwarding Match List to the profile
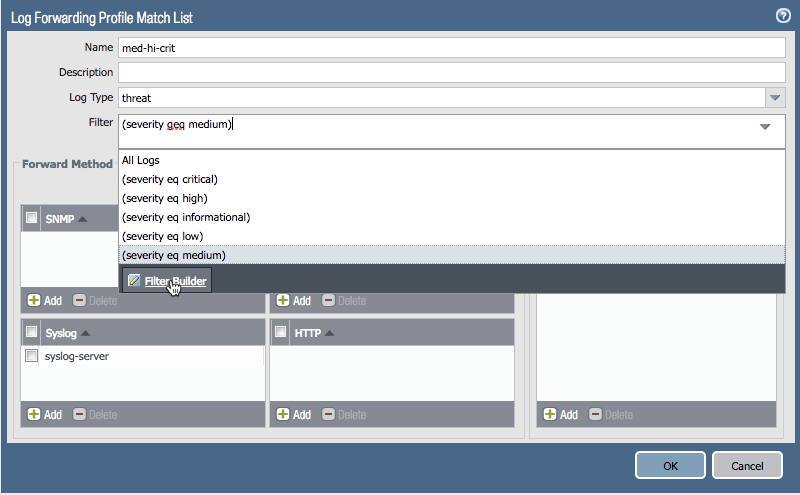 add the syslog server and select a desired (if any) filter
add the syslog server and select a desired (if any) filter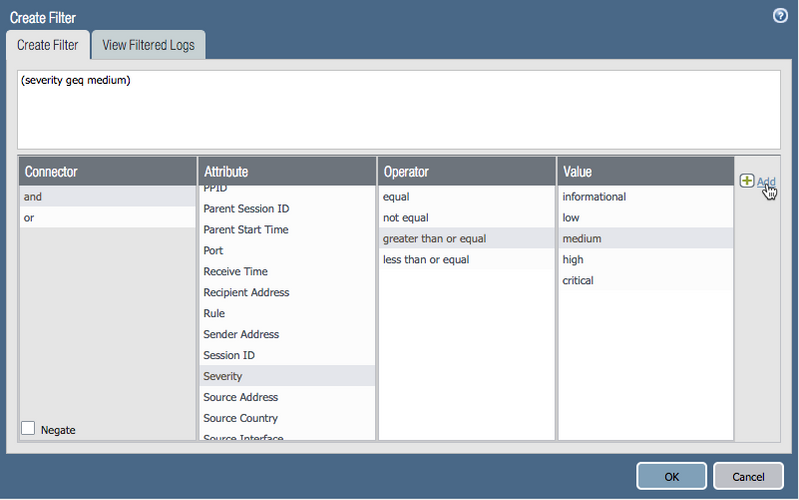 Use the filter builder to add more filtering parameters for logs to be forwarded
Use the filter builder to add more filtering parameters for logs to be forwarded
Once configured, the log forwarding should look like the following
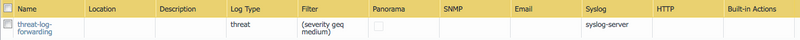
Security Rule
Go to Policies > Security Rule
Select the rule for which the log forwarding needs to be applied. Apply the security profiles to the rule.
Go to Actions > Log forwarding and select the log forwarding profile from drop down list.
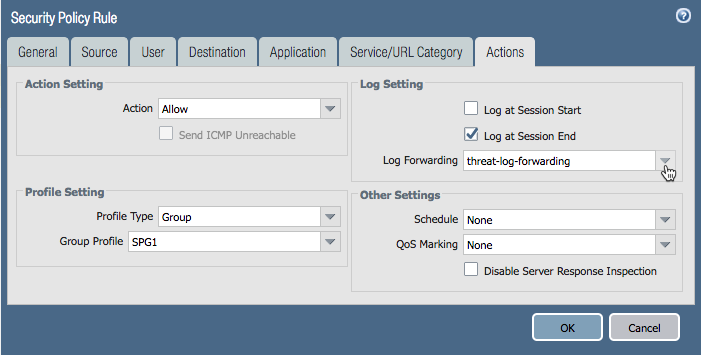
Commit the configuration