On the Web UI:
- Navigate to Network > DNS Proxy.
- Click Add to bring up the DNS Proxy dialog.
- Select the interfaces on which DNS proxy should be enabled. In the below figure the DNS proxy is enabled on interfaces ethernet 1/2 and 1/3.
- Select the primary and secondary servers where the firewall should forward DNS queries.
The example shows a configuration where DNS proxy is enabled on the ethernet 1/2 and 1/3 interfaces. The primary DNS server is configured with 10.0.0.246.
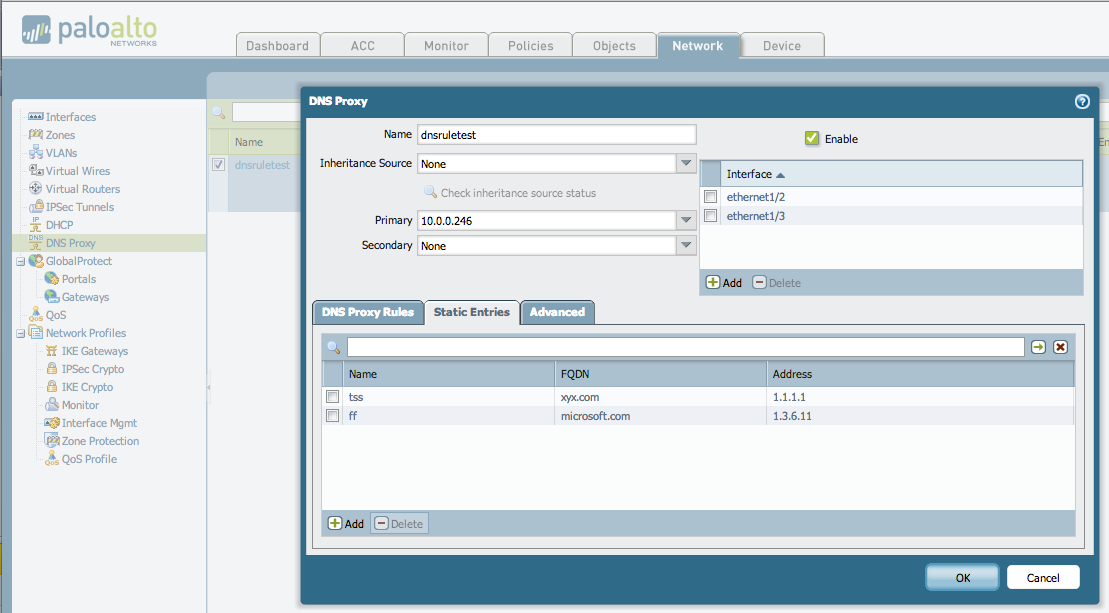
- Static entries can be added to the DNS proxy. Enter the FQDN and associated address information in the Static Entries tab.
- The Palo Alto Networks firewall can be configured to cache the results obtained from the DNS servers. For information on configuring DNS caching, refer to How to Configure Caching for the DNS Proxy.
Note: If a DNS entry is not found in the cache, then the domain is matched against the static entries list. If a match occurs, then the corresponding address is served. If there is no match, the DNS request is forwarded to the configured Primary or Secondary DNS servers. The source of the DNS query is the ingress interface of DNS request which, in this case, would be either ethernet1/2 or ethernet1/3.
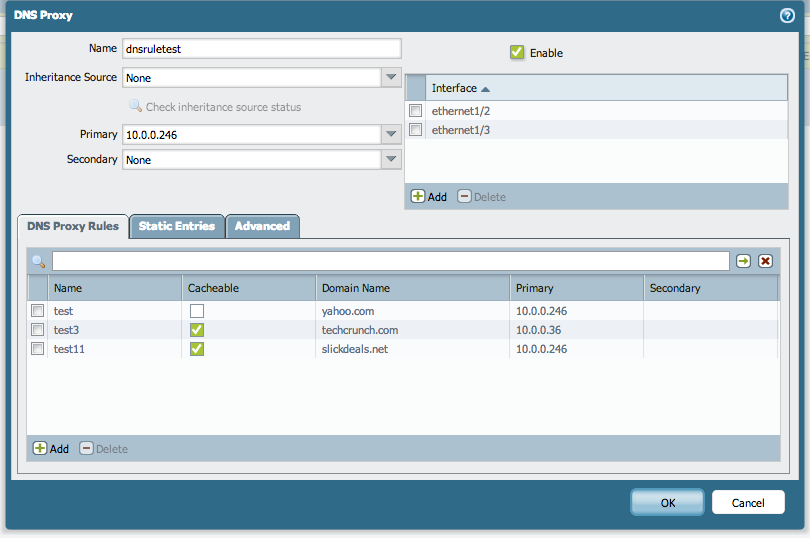
- By configuring rules under the DNS Proxy Rules tab, the Palo Alto Networks firewall can forward selective domains to DNS servers different from the configured primary and secondary. The example shows a DNS proxy rule where techcrunch.com is forwarded to a DNS server at 10.0.0.36.
Note: The Palo Alto Networks firewall can also perform reverse DNS proxy lookup. On the client side, configure the DNS server settings on the clients with the IP addresses of the interfaces where DNS proxy is enabled.
On the CLI:
> configure
# set network dns-proxy dnsruletest interface ethernet1/2 enabled yes
# set network dns-proxy dnsruletest default primary 10.0.0.246
# set network dns-proxy dnsruletest static-entries tss domain xyx.com address 1.1.1.1
# set network dns-proxy dnsruletest domain-servers test cacheable no primary 10.0.0.246 domain-name yahoo.com
# commit
Verification
Verify the DNS proxy using the following commands:
> show dns-proxy statistics all
Name: dnsruletest
Interfaces: ethernet1/2 ethernet1/3 ethernet1/4
Counters:
Queries received from hosts:12
Responses returned to hosts:12
Queries forwarded to servers:6
Responses received from servers:6
Queries pending:0
TCP:0
UDP:0
--------------------------------------
> show dns-proxy cache all
Name: dnsruletest
Cache settings:
Size:1024 entries
Timeout:14400 seconds
Domain IP/Name Type Class TTL Hits
------------------------------------------------------------------------------
2.2.2.4.in-addr.arpa b.resolvers.level3.net PTR IN 60598 1
For more debugging information, look at the dnsproxyd.log:
> tail follow yes mp-log dnsproxyd.log
By default, same zone traffic is allowed, however, if there is a "deny all" rule set, then a security rule is required to allow traffic. Add a security rule to allow DNS traffic.
Note: DNS proxy rules do not apply to traffic initiated from the firewall's management interface. For example: From the management interface, an attempt to ping something defined in the DNS proxy does not use the DNS proxy rule, but rather the DNS values from the server instead.
See Also
Can Management Interface use DNS Proxy Rules And Static Entries through DNS Proxy Object?
Blocking Suspicious DNS Queries with DNS Proxy Enabled
owner: sdurga