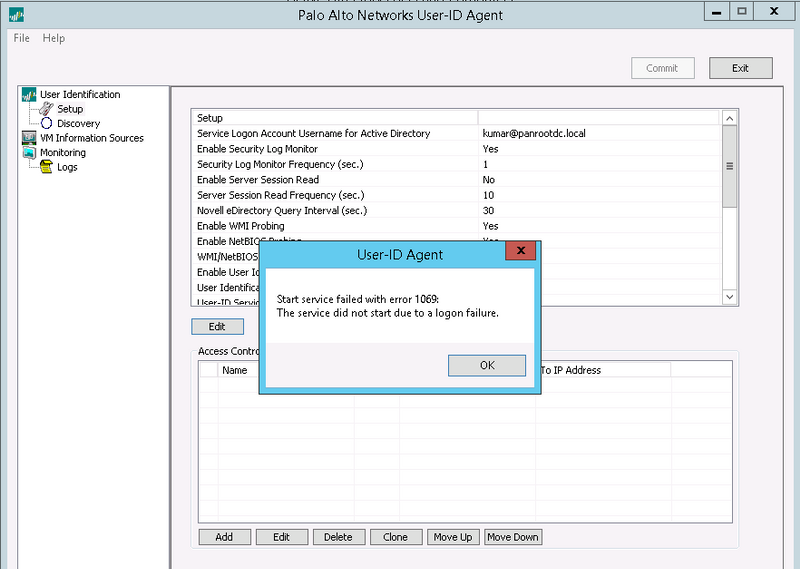
This article outlines the steps required to install the UserID Agent and account permissions required for it to function properly. If not all access is granted, you may encounter the following error: "Start service failed with error 1069: The service did not start due to a logon failure."
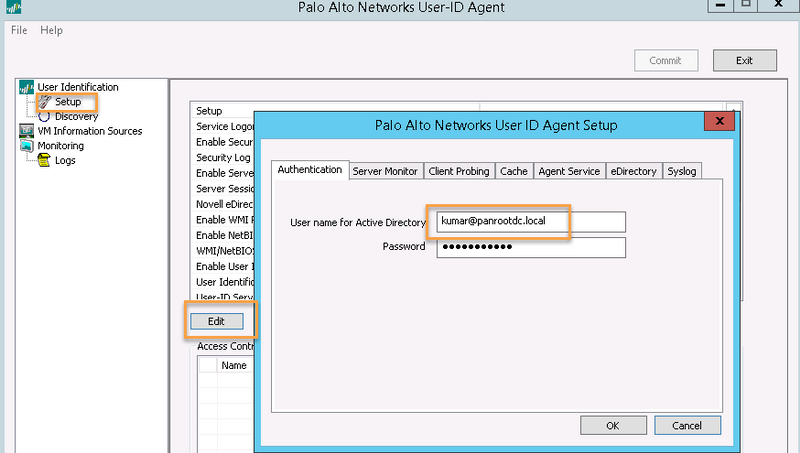
In this article the example service account is 'kumar@panrootdc.local'.
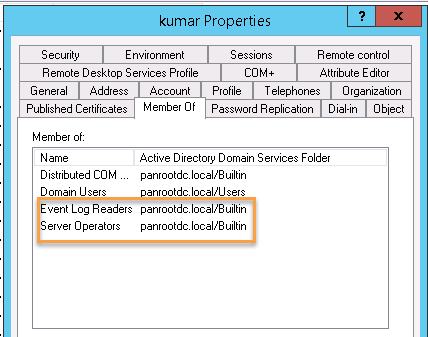
Step 1. Make sure the account you are using in the User-id agent is part of 'Event log reader' and 'server operator.' In this example "kumar@panrootdc.local" should be part of "server operator", "event log reader"
# Please note that 'server operator' is required for Agent-less UserID. But it is optional for Windows based Used ID agent.
Step 2. Account should be to log on as a service. Open Administrative Tools, then open Local Security Policy.
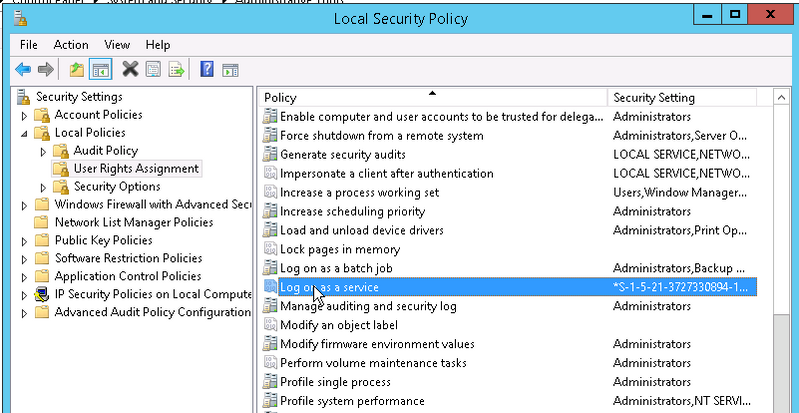
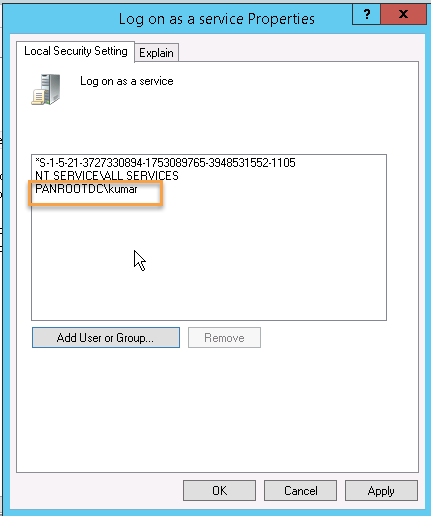
Go to Local Policies > User Rights Assigment. Find Log on as a service. Double click and add the account to Local Security setting.
Please also make sure Deny Log on as a service does not have ServiceAccount user listed as a member
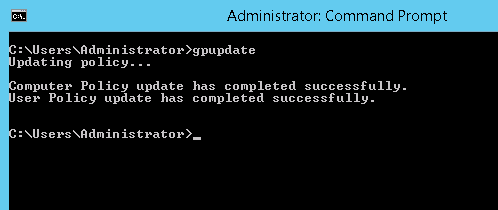
Step 3: Open cmd in Administrator mode and perform a 'gpupdate'. Otherwise, it will take time for the changes to take effect.
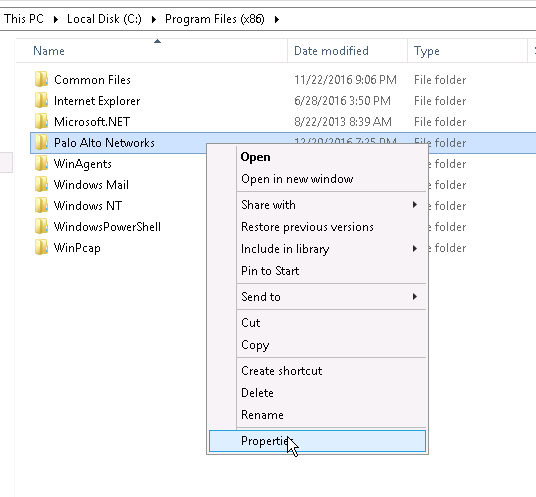
Step 4. The account should have permission to the folder where the User ID agent is installed. To give permission, go to the folder where User-ID agent is installed and grant the required permission:
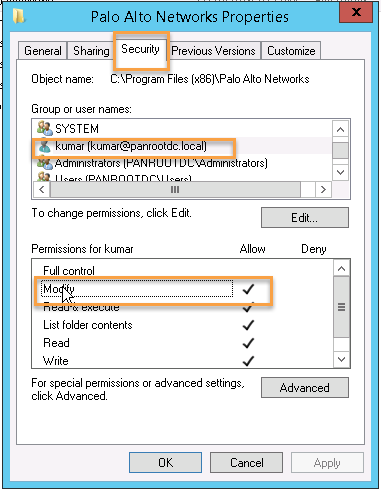
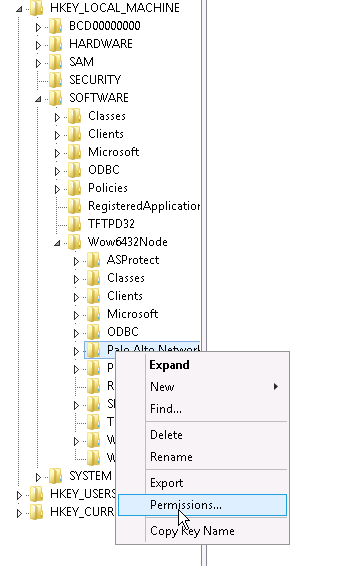
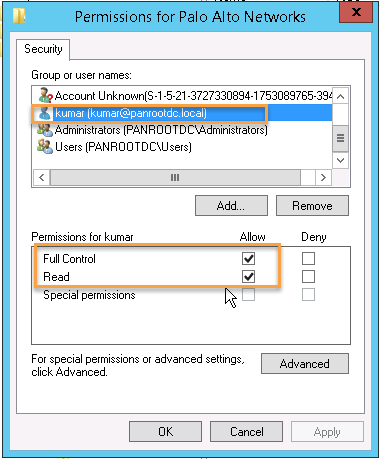
Step 5. The account should have permission to registry: Locate the Palo Alto Networks folder in
Computer\HKEY_LOCAL_MACHINE\Software\Palo Alto Networks
OR
Computer\HKEY_LOCAL_MACHINE\Software\WOW6432Node\Palo Alto Networks
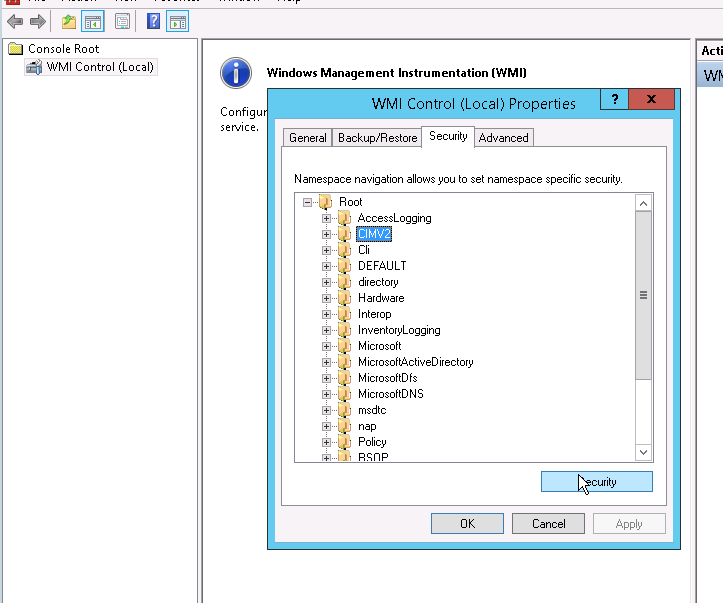
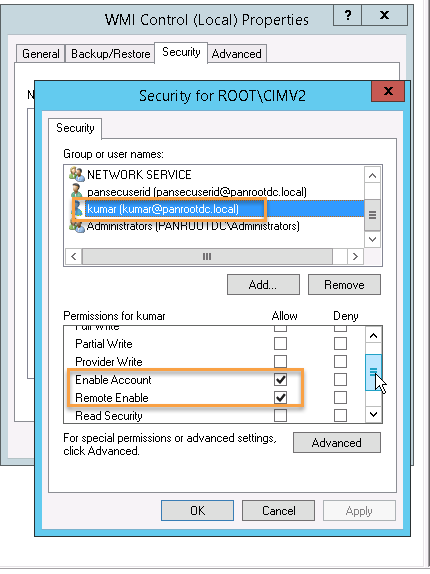
Step 6. Give proper permission to the account for WMI CIMv2: In 'run' type 'wmimgmt.msc' and hit enter.